Hacker Targeting Unfixed WordPress Plugin Vulnerability That CVE and Others Claim Has Been Fixed
For some time, we have been seeing a hacker probing for the usage of various WordPress plugins with known vulnerabilities across numerous websites. Earlier this month, we noted that the hacker was targeting a plugin that had an unfixed known vulnerability and that the plugin had remained in the WordPress Plugin Directory despite that. That isn’t a one-off issue. Today we saw the same hacker probing for usage of the ReviewX plugin, which is still in the plugin directory. That isn’t a surprise, as the plugin has recently had an authenticated SQL injection vulnerability disclosed. More problematically, as we warned about two weeks ago, it was incorrectly claimed to have been fixed.
In our previous post, we noted that the incorrect claim that this had been fixed had been included in the CVE system, which is funded by the US government. CVE is a system that is treated as a reliable and notable source of information on vulnerabilities, for reasons we can’t understand. In reality, they allow just about anyone to add data to the system and there isn’t a functioning system to make sure it is accurate. With this vulnerability, we reported that the information was incorrect to the company that put the information into the CVE system, but it hasn’t been corrected. Here is the current state of the entry, still claiming that this affected versions before 1.6.4:
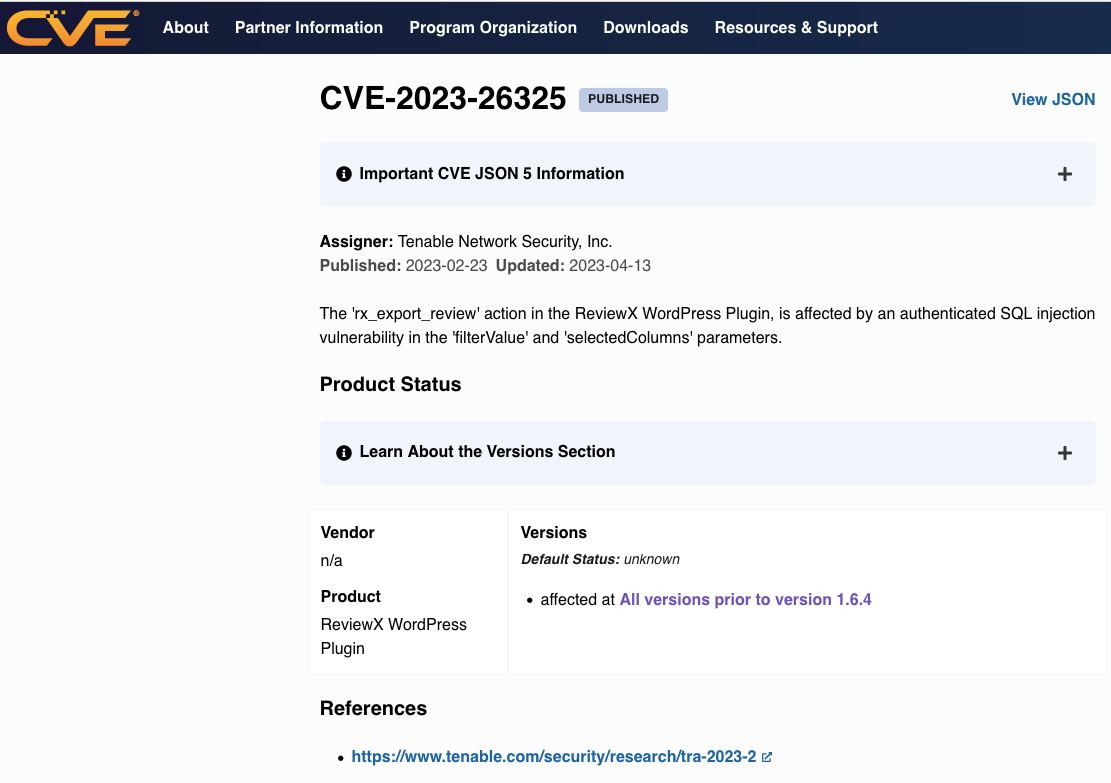
It still exists as of the latest version 1.6.7.
The claim that it affects “All versions prior to version 1.6.4” isn’t true coming from the other direction either, as the vulnerability involves functionality that was only introduced in version 1.5.7. We can’t emphasize enough that CVE’s information isn’t any way reliable.
CVE claims to have a process for disputing information, but it doesn’t work and CVE won’t even respond when that is brought up with them.
Before we publicly warned the vulnerability hadn’t been fixed, we contacted the plugin’s developer about that and offered to help them fix it. We haven’t gotten any response.
Patchstack Isn’t Warning About This
In our previous post, we noted that a WordPress plugin vulnerability data provider from the company run by the head of WordPress, WPScan, was telling people that the vulnerability had been fixed. The only source they cited was CVE, despite CVE’s information being known to not be reliable.
With another data provider, Patchstack, they make this extraordinary claim about their service:
Be notified instantly when there is a new security vulnerability present on any of your sites. Patchstack monitors security of all WordPress core, plugin and theme versions in real-time.
None of that is true (if it was true, then vulnerabilities in WordPress plugins would be a thing of the past), but they haven’t even warned their customers about the vulnerability:

Not The Only Inaccurate CVE Entry We Have Run Across Recently
In December, the aforementioned WPScan issued a CVE ID, CVE-2022-4715, for a vulnerability in another WordPress plugin, Structured Content. The entry claims the vulnerability had been fixed in version 1.5.1. We checked over that earlier this week, as one of our customers started using the plugin. What we found was that the vulnerability hasn’t been fixed.
Make Sure to Get Your WordPress Plugin Vulnerability Data From a Reliable Source
With known unfixed vulnerabilities like both of these, keeping WordPress plugins up to date won’t protect you. Monitoring to see if plugins you use have been closed on the WordPress Plugin Directory won’t protect you either, as both are still available. This is where WordPress plugin vulnerability data providers should be able to protect you. But with the Structured Content vulnerability, both the previously mentioned providers, WPScan and Patchstack, as well as Wordfence, are claiming the vulnerability has been fixed. So you need to make sure that the provider is doing the verification work they claim to do. As far as we are aware, we are the only provider that does that.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade