Catching a Future Vulnerability in a WordPress Plugin With Our Plugin Security Checker
One of the tools we have to try to help make WordPress plugins more secure is our Plugin Security Checker, which flags possible security issues in WordPress plugins. From time to time, we spot check the results of plugins from the WordPress Plugin Directory being run through that to make sure we are limiting mistakes it might make. Through that we saw that the 90,000+ install plugin LearnPress had insecure code that could lead to reflected-cross-site scripting (XSS) because user input was being output without escaping it:
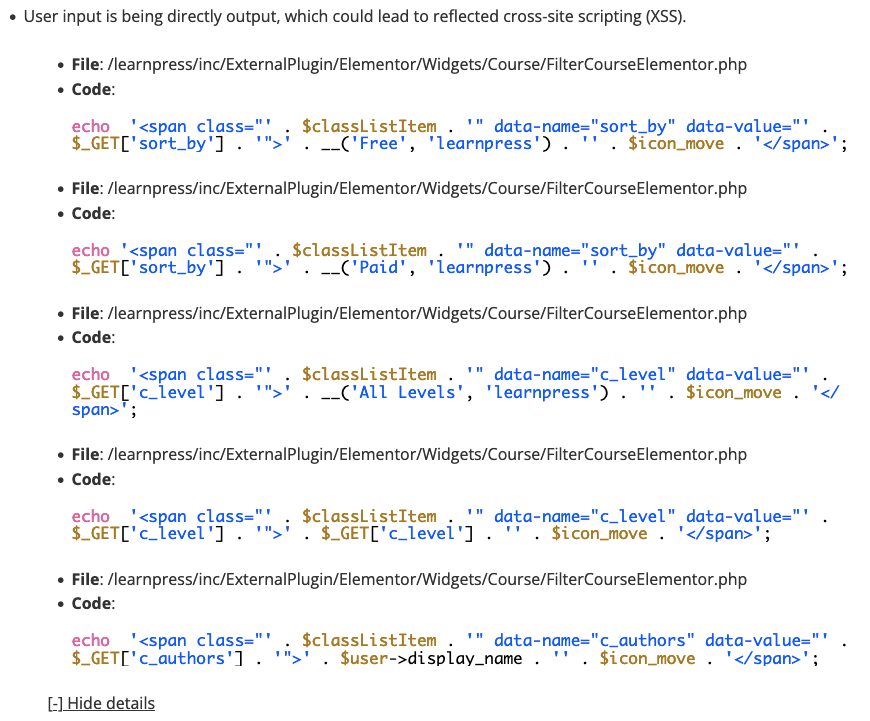
In looking further to see if there was a vulnerability caused by that, we found that the code was recently added to the plugin, but isn’t yet accessible. The relevant changelog when it was added reads “Dev: widget elementor filter courses.” It’s unclear why apparent development code was placed in the plugin at this time, but only made accessible if you modified a plugin file. But it was.
Once we figured out how to enable that, we confirmed that there is a reflected cross-site scripting (XSS) issue with the plugin Filter Courses Elementor widget, if it was made accessible. We have notified the developer of the issue and offered to help them address it.
That security problem maybe isn’t all that surprising, as the developer has repeatedly had to release security updates for the plugin, including for a recent vulnerability that our firewall plugin then stopped a hacking attempt against.
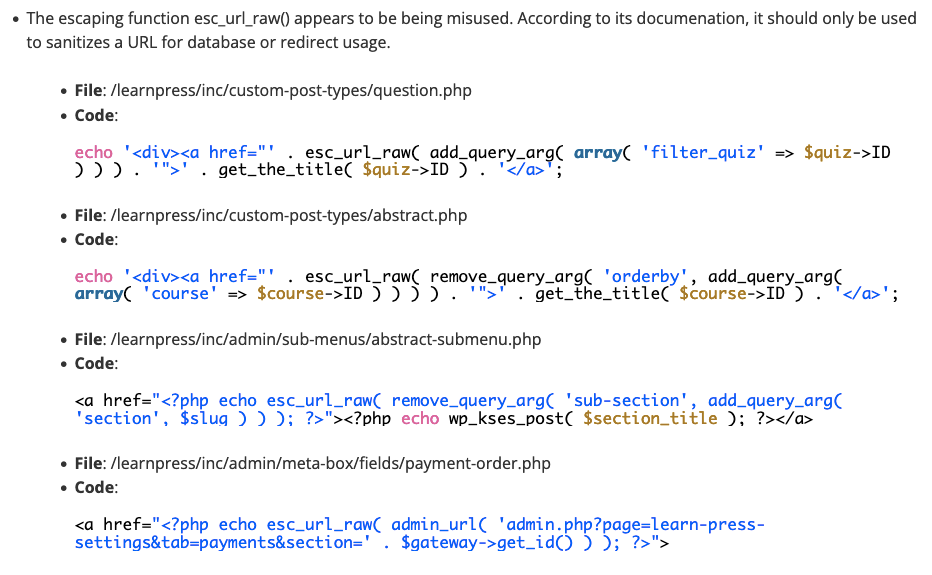
The tool also flags numerous instances of misuse of the esc_url_raw() (which we discussed recently):