At Least 10,000 WordPress Websites Still Have Exploited Versions of Icegram Express Plugin Installed
Yesterday, we detailed our findings on a SQL injection vulnerability that had been in the WordPress plugin Icegram Express, after having a hacker try to exploit it on our website. The vulnerability was addressed enough to stop exploitation on March 28, but hasn’t been fully fixed yet (neither has another vulnerability). Beyond the incomplete fix, what is concerning with this situation is that so many WordPress websites still have a vulnerable version of the plugin installed.
Based on data provided by WordPress, we can get some idea of how many websites still have a vulnerable version. The active installation count for the plugin is 90,000+. So somewhere between 90,000 and 100,000 websites. They also provide data on active versions of the plugin:
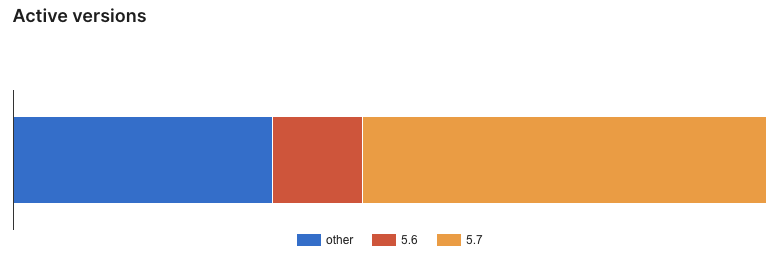
Unfortunately, that isn’t all that granular, making getting a good count of vulnerable websites not possible based on that. But we can get some idea.
The code that allowed the attacks we saw was added in version 5.4.13 of the plugin, which was released in September 2022 (the first function called was set to its present name in version 5.5.6). The incomplete fix was done in version 5.7.15.
The data says that 12.0% of the active installs are at version 5.6, of which all versions are vulnerable. If there are 90,000 installs, that would put the number of websites with a vulnerable version at 10,800. Of the remaining 88% of active installs, we know that tens of thousands of websites are not vulnerable, based on the download chart for the plugin, which counts the plugin being updated. As over 20,000 downloads are happening when new versions are being released:

Based on the number of websites still on 5.6, is seems reasonable to think that there are plenty of additional websites running other older versions of the plugin that are vulnerable.
Probably not helping the situation is that those running an older version are not being warned in WordPress that they are using a version of the plugin known to be exploited or even that it is known to be vulnerable: