WP Tavern’s Nathan Wrigley Highlights Duo of Companies Handling Security Badly as Example of Providing Better Security Outcomes
A new legal filing from lawyers representing Matt Mullenweg claims that he loves the WordPress community. That is hard to square with so much of what he does. For more than a decade, he has run a WordPress news outlet that fails to follow the basic journalistic standard of disclosing when the news outlet is covering the owner of the news outlet and related parties. That news outlet being the WP Tavern, which is also included in the WordPress news feed that he controls without a disclosure of the situation either. In addition to the news coverage, the WP Tavern has a podcast done by Nathan Wrigley. He isn’t someone who has shown any concern for the accuracy of what he covers. The latest podcast episode shows that off.
Before we get in to the podcast episode, let’s step back in time to April 2022. That month, hackers started targeting a vulnerability in the very popular Elementor plugin. The vulnerability allowed arbitrary code to be run on the website by anyone logged in to WordPress with any user role that had access to the admin area of WordPress. Normally anyone logged in to WordPress has access to the admin area. That vulnerability was caused in part by Elementor failing to implement a very basic security check to make sure only a user with an intended capability could access functionality. Another part of the cause was that Elementor was leaking a security nonce to users that shouldn’t have had access to it.
That these issues occurred in a plugin with millions of installs is concerning. In a reasonable world, it would have led to an overhaul in Elementor’s handling of security and implementing practices to prevent those issues from occurring again. That isn’t what happened.
At the end of January, we found that the leaking of nonces to anyone logged in to WordPress was still an issue. We reached out to Elementor about that, but the issue still hasn’t been resolved. Their response suggested it has already been reported to them by that time.
If you were to try to report that issue to them now, you would find that Elementor isn’t actually properly handling reporting security issues to them. On their Contact page, you would think that they are, as they have a link to create a ticket to report security issues:
Clicking that link shows something very different. They are directing to report security issue through bug bounty programs:
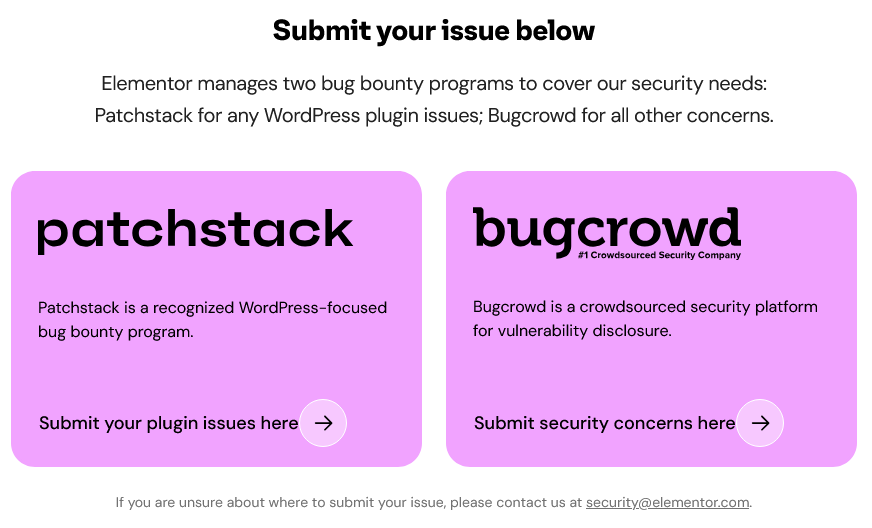
While they claim to manage those. In reality, the one for WordPress plugins is managed by Patchstack. Considering that Patchstack has a long track record of lack of concern about handling vulnerabilities, that is incredible. It gets worse, as they don’t actually accept reports of security issues, only certain types of vulnerabilities:
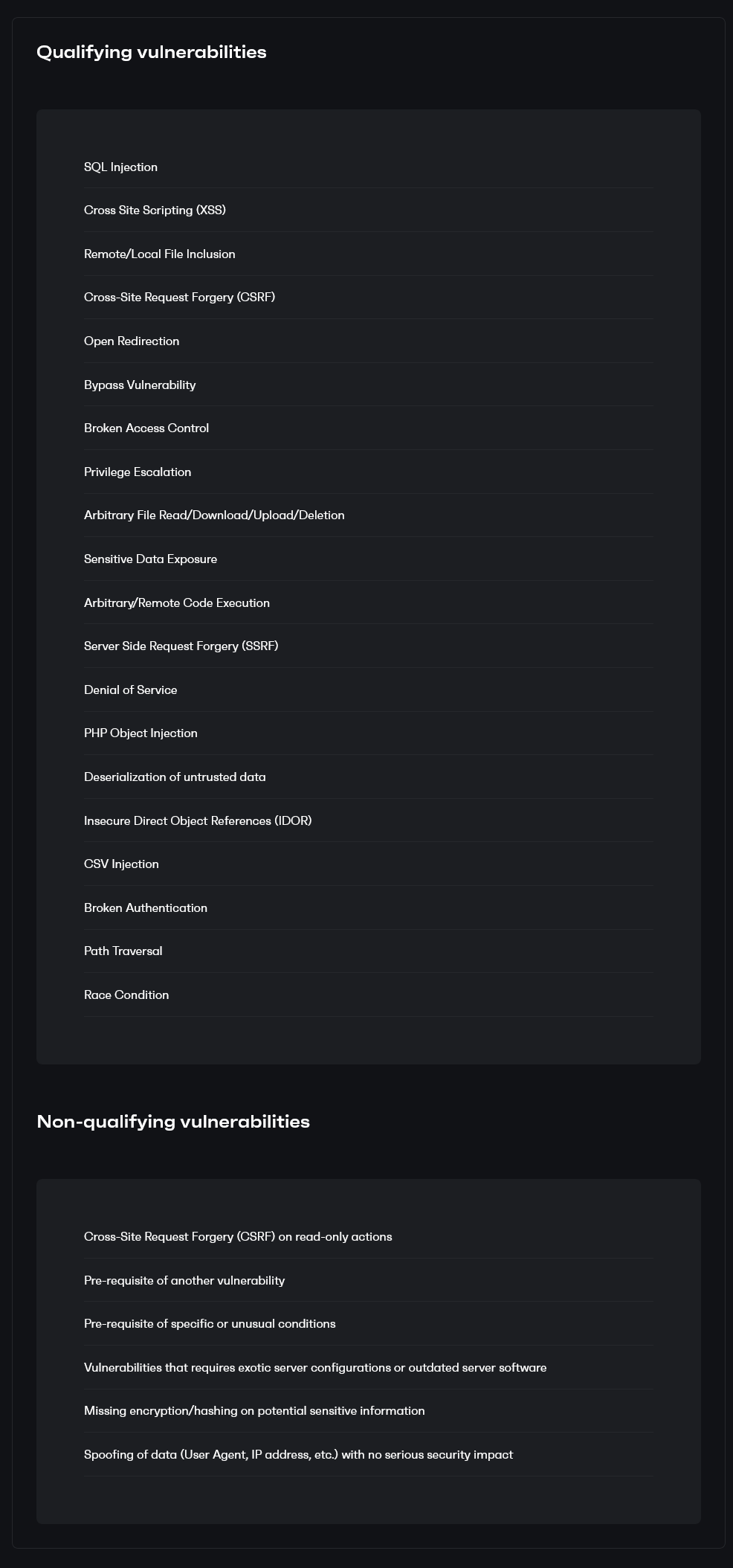
That means you can’t report this type of issue. Even though, history has shown that it can lead to widely exploited vulnerabilities.
That you can’t report it makes sense for Patchstack, since they only want vulnerabilities reported to them so that they can sell access to information to information about them. It doesn’t make sense for a plugin developer that cares about security at all, since they would actually want to fix those issues.
Elementor’s team up with Patchstack hasn’t gone well. In December, Patchstack disclosed there was a vulnerability in Elementor before there was a fix available. Patchstack’s partnership with the developers of other plugins has produced bad results as well.
The latest WP Tavern podcast is about their partnership, but Nathan Wrigley paints it as being something very different from the reality:
We also get into how Miriam’s team at Elementor collaborates with Patchstack to ensure rapid and professional handling of vulnerabilities, enhancing security for their 17 million installations. The partnership between Elementor and Patchstack is a great example of how different companies within the WordPress community are able to work together to provide better outcomes for their users.
As we noted before, a plugin developer that cares about security wouldn’t be directing vulnerability reports away from themselves to someone selling access to information about vulnerabilities. But Nathan Wrigley promotes as something other than an indication that the developer doesn’t care about security:
Miriam and Oliver joined me at WordCamp US 2024 in Portland, where they did a presentation discussing the processes needed to enhance open source plugin security and the advantages of leveraging bug bounty partnerships. Their collaboration brings to light the importance of integrating security solutions within the WordPress ecosystem, especially for companies with a footprint as large as that of Elementor.
It would appear that Nathan Wrigley didn’t bother to do any due diligence here. Elementor is known for handling security badly. So badly that in April of last year, we issued a warning about their handling. Patchstack’s CEO, who was one of the guest on the podcast, has indirectly admitted that partnerships like this are not ethical.
An more appropriate partnership would be for Elementor to hire a security provider to do a security review of their plugin. From one provider that has a long track record of doing reviews, it would cost $700. It is a price they could afford after having raised $65 million. The chances of them doing something that would actually improve the security of their plugin are unlikely to happen when they can get positive coverage for cutting corners when it comes to security by Nathan Wrigley.
Plugin Security Scorecard Grade for Elementor
Checked on August 29, 2024See issues causing the plugin to get less than A+ grade