WordPress Firewall Plugin Claimed to Protect Against “Any Threat” Doesn’t Stop Even One Simulated Attack From Firewall Testing Tool
Starting late last year, there has been a significant increase in the number of plugins being submitted to the WordPress Plugin Directory. That appears to be largely caused by the ease of AI to generate WordPress plugins and not growth of WordPress ecosystem. That has multiple implications for the security of WordPress websites. One is that yet more security plugins making great promises as to the protection they offer, while not delivering on it. Or even introducing additional security risk.
Considering that AI builds things based on existing code, you would likely also see that these plugins would be focused on common security features already known to offer limited to no security value. While we can’t say which new security plugins are generated by AI, we can say that new security plugins that could have been generated by AI are providing useless protection. Both WPS Protect: Login URL & Security Headers, which was released last week, and Iron Security, which was released in March, claim to offer additional protection by adding the security header X-XSS-Protection to websites. That clearly isn’t going to offer protection considering that no web browsers support that header anymore:
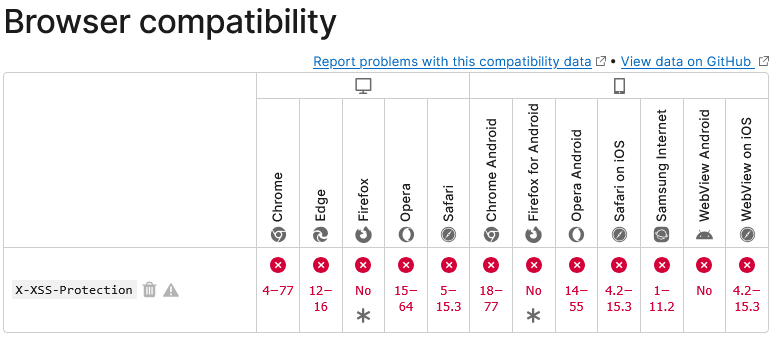
Even when they did, the feature the header could be used to turn off or on, was already enabled by default. It was subsequently removed from web browsers because of a lack of protection offered and additional security risk it could create.
Based on that, it would appear the developers of these plugins lack a basic understanding of website security. That is despite Iron Security being marketed as developed “by team with cyber security background.”
Iron Security is also marketed on the plugin directory as being a firewall and marketed as protecting against any threat:
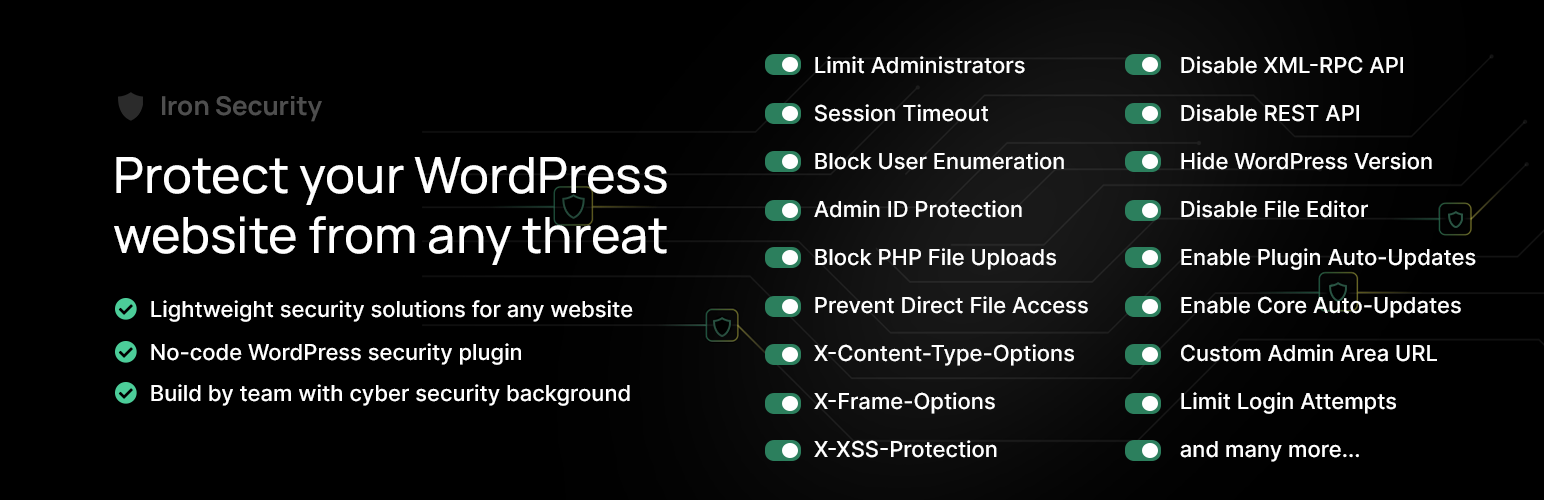
The claimed features of the plugin don’t appear to be related to a firewall, but we were curious to see what would happen when testing the plugin against a new tool we have just have made publicly available. That tool tests a WordPress website to see if there is a firewall that effectively blocks simulated attacks. The main limitation with the tool in comparison with our internal tooling for testing firewall effectiveness is that it can only simulate attacks that don’t require vulnerable code running on a website.
The tool currently has 127 tests. Many of which are variations on the same test, but varying things in a way that poorly developed firewalls are known to fail to catch. Both because they fail to handle non-standard payloads, but also because they only provide protection for certain types input. We tested Iron Security and found it failed to stop any of the attacks. That is in line with it not having a firewall. It also then clearly doesn’t protect WordPress websites from any threat as claimed.
Its logging did provide a warning for two of the tests. That isn’t a great result, as there are a lot more than two tests very similar to that.
WordPress Plugin Directory Should Require Evidence of Effectiveness
A security plugin being marketed so dishonestly seems rather problematic for WordPress. Either you have developers who are intentionally dishonest or that are so unaware of security they don’t know how obviously dishonest they are. In either case WordPress is then providing more visibility to security solutions. Better addressing this would be quite easy. Simply require that developers provide evidence backing up strong claims about the effectiveness of their plugins. Claims like the one made by this plugin certainly don’t have any evidence backing them up. How could you even know that something protect any type of attack?
Considering the team running the plugin directory’s unfortunate long history of dishonesty and poor handling of security, that seems unlikely to happen. Our new tool does provide additional option for evaluating if security plugins are delivering on their promises.