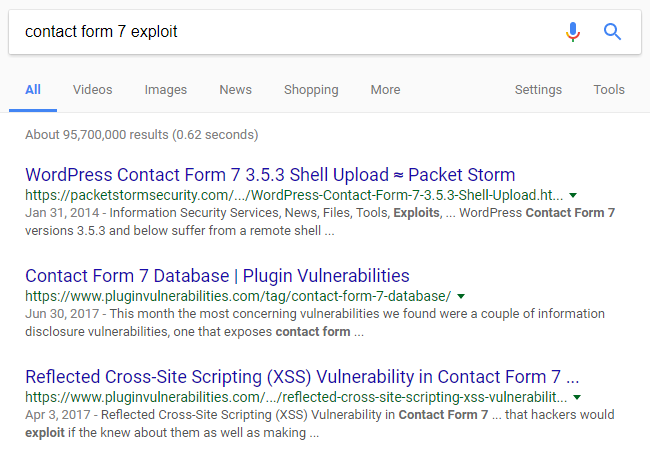
Google Not Always Providing Really Relevant Results When Searching For WordPress Plugin Vulnerabilities
In looking at recent traffic from Google coming to our website by way of the Search Analytics portion of Google’s Search Console we noticed that for three of the top five sources of clicks to our website relate to something we don’t have any really relevant content for. The queries all relate to the plugin Contact Form 7:
- contact form 7 vulnerability
- contact-form-7 exploit
- contact form 7 exploit
We don’t have any posts that relate to vulnerabilities in that plugin, the closest that we come to that are some posts about vulnerabilities in software that works with it, which have “Contact Form 7” in their name. In looking at the results for the above queries, the pages from our website do it fact relate to one of those plugins:
While it might be somewhat relevant to show results from plugins that work with Contact Form 7 if there were not disclosed vulnerabilities or exploits for Contact Form 7, it seems unlikely that those pages related to Contact Form 7 Database would be relevant for many people doing the searches considering that according to wordpress.org there are 5+ million active installs of Contact Form 7 and only 7,000+ active installs for Contact Form 7 Database.
One of the problems with these types of results is that people do not appear to always be looking closely at the results before taking some further action. A month ago someone posted on the support forum for Contact Forum 7 claiming they found an “article from about 7 weeks ago talking about SQL injection in Contact Form 7”. They went to on to ask
And is there an update coming out to fix it? Hopefully you can identify what needs to be fixed.
What they were referring to was a post we put out with the details of a fixed vulnerability in another related plugin, Save Contact Form 7. That plugin is also is much less popular than Contact Form 7, which only 10,000+ active installs.
Considering the popularity of Contact Form 7 and that there haven’t been any recent disclosures of vulnerabilities in it, the chances that a security review would find any issues in the plugin are low, but if you are looking for an assessment of the security of the plugin you can order a security review of it (or any other WordPress plugin for that matter) from us. That currently includes checking for the following issues:
- Insecure file upload handling (this is the cause of the most exploited type of vulnerability, arbitrary file upload)
- Deserialization of untrusted data
- Security issues with functions accessible through WordPress’ AJAX functionality (those are a common source of disclosed vulnerabilities these days)
- Persistent cross-site scripting (XSS) vulnerabilities in publicly accessible portions of the plugin
- Cross-site request forgery (CSRF) vulnerabilities in the admin portion of plugins
-
SQL injection vulnerabilities (the code that handles requests to the database)
-
Reflected cross-site scripting (XSS) vulnerabilities
- Security issues with functions accessible through any of the plugin’s shortcodes
- Security issues with functions accessible through the admin_action action
- Security issues with import/export functionality
- Security issues with usage of is_admin()
-
Lack of protection against unintended direct access of PHP files
- Insecure and unwarranted requests to third-party websites