Authenticated Local File Inclusion (LFI) Vulnerability in ChimpMate
In seeking to continue to improve our Plugin Security Checker, which does automated checks to try spot potential security issues in WordPress plugins, we log the results of checks of plugins in the Plugin Directory. The plugin ChimpMate was recently run through that and one of the issues identified in that was a possible local file inclusion vulnerability:
Since the check for that issue is based on a fairly limited number of previously identified vulnerabilities we decided to check on that to see if what was flagged was correctly identified.
For someone with the necessary knowledge to review possible security issues more closely they can use the Developer Mode of the tool, which is available to customers of our service, to see the details of what lead to the tool warning of the possible issue. What was shown was this:
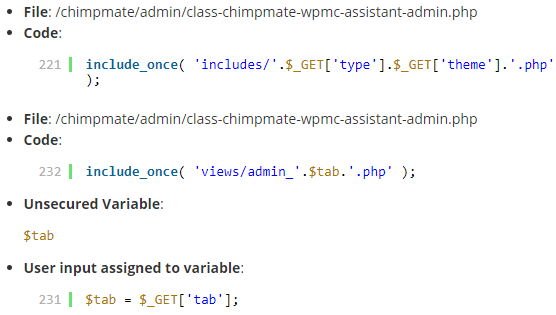
In both of the instances shown there, user input is used to include a file through the function include_once(), in the first instance the user input is directly used and in the second it used through a variable. Those both would be accurate identifications of a possible issue.
When then decided to take a look to see if there was a vulnerability caused by either of those.
The first instance was located in the function preview() in the file /admin/class-chimpmate-wpmc-assistant-admin.php and looked like this:
219 220 221 222 223 | public function preview(){ if(!isset($_GET['type']) || !isset($_GET['theme']))die(); include_once( 'includes/'.$_GET['type'].$_GET['theme'].'.php' ); die(); } |
That code simply checks if the GET inputs “type” and “theme” exist and if they do, it uses those with the include_once() function.
That function is accessible to anyone logged in to WordPress through its AJAX functionally:
52 | add_action('wp_ajax_chimpmate_prev', array( $this, 'preview' ) ); |
That means there is authenticated local file inclusion vulnerability, which could allow an attacker who is able to log in to WordPress to cause any .php file on the website to be run. Through cross-site request forgery (CSRF) it would also be possible for an attacker to cause anyone logged in to WordPress do the same thing.
The second instance identified by the tool could be exploited in the same way.
We notified the developer of the issue a week ago. We haven’t heard back from them and no new version has been released to fix the issue. In line with our disclosure policy, which is based on the need to provide our customers with information on vulnerabilities on a timely basis, we are now disclosing this vulnerability.
Proof of Concept
The following proof of concept will cause a file named test.php in the root directory of the WordPress installation to be included, when logged in to WordPress.
Make sure to replace “[path to WordPress]” with the location of WordPress
http://[path to WordPress]/wp-admin/admin-ajax.php?action=chimpmate_prev&type=../../../../../&theme=test
Timeline
- June 11,2018 – Developer notified.