RIPS CodeRisk Doesn’t Look To Produce All That Reliable Risk Scores for WordPress Plugins
While so much of the security industry seems to have no interest in providing accurate information about security, for those that do care, if our experience is any indication, it is difficult to find a way to present information in a way that provides the proper concern without creating unnecessary fear due to misinterpretations of the information presented and many people’s belief that they have a better understanding of security than they really do. That seems to come in to play with something we ran across recently in our monitoring of the WordPress support forum for indication of security issues in WordPress plugins.
Yesterday a thread was started with the following:
I was browsing this directory today to look at plugins that my team regularly uses and noticed that this plugin has a very high vulnerability score:
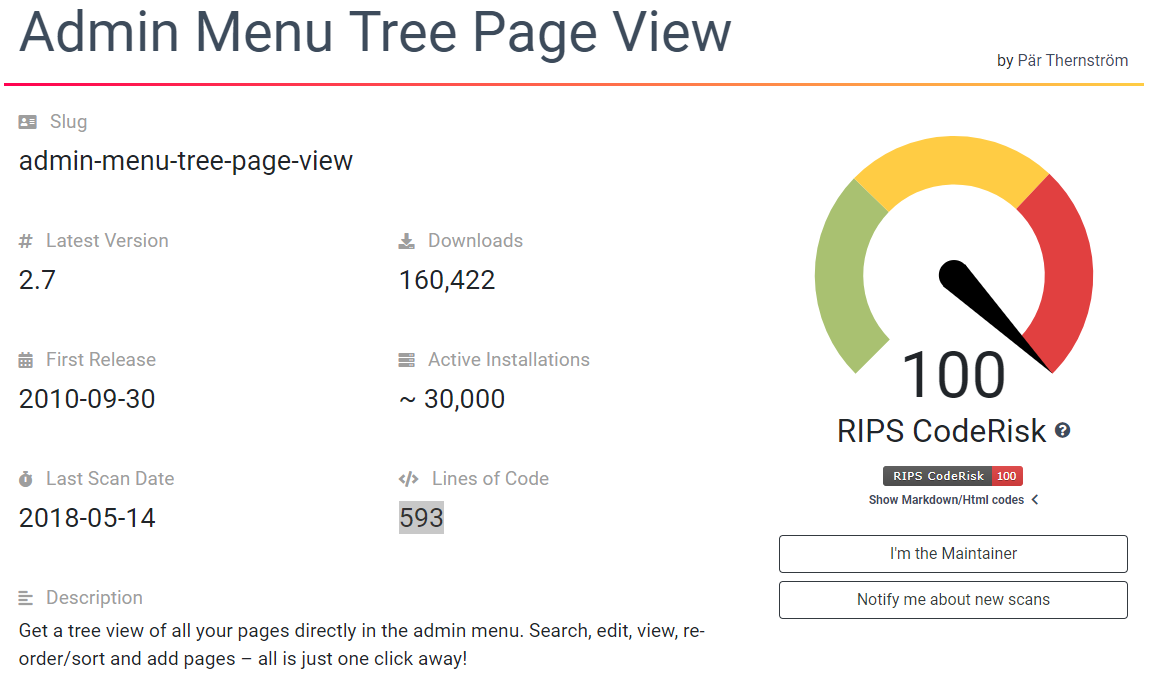
https://coderisk.com/wp/plugin/admin-menu-tree-page-view100 is the highest possible and may be due to the high amount of DB queries performed.
Is this something that can be looked into for future updates? I’m afraid the convenience of this plugin does not outweigh any security risk, so I’d really love to see it updated. Thanks!
When you follow the link in that you see the following information:
No information is provided as to what lead to that score and there is actually no mention of database queries. We are not sure why simply having a large amount of database queries would be a security risk, but considering that the result indicates that there are only 593 lines of code in the plugin it seemed unlikely that there were that many database queries.
In doing a quick look over the code we found only five database queries that appear to run and they all seem properly secured using a prepared statement:
392 | $wpdb->query( $wpdb->prepare( "UPDATE $wpdb->posts SET menu_order = menu_order+2 WHERE post_parent = %d AND menu_order >= %d AND id <> %d ", $ref_post->post_parent, $ref_post->menu_order, $ref_post->ID ) ); |
434 | $wpdb->query( $wpdb->prepare( "UPDATE $wpdb->posts SET menu_order = menu_order+1 WHERE post_parent = %d", $ref_post->ID) ); |
549 | $wpdb->query( $wpdb->prepare( "UPDATE $wpdb->posts SET menu_order = menu_order+1 WHERE post_parent = %d", $post_ref_node->post_parent ) ); |
553 | $wpdb->query( $wpdb->prepare( "UPDATE $wpdb->posts SET menu_order = menu_order+1 WHERE menu_order >= %d", $post_ref_node->menu_order+1) ); |
570 | $wpdb->query( $wpdb->prepare( "UPDATE $wpdb->posts SET menu_order = menu_order+2 WHERE post_parent = %d AND menu_order >= %d AND id <> %d ", $post_ref_node->post_parent, $post_ref_node->menu_order, $post_ref_node->ID ) ); |
There is also one commented out database query:
573 | #$wpdb->query( $wpdb->prepare( "UPDATE $wpdb->posts SET menu_order = %d, post_parent = %d WHERE ID = %d", $post_ref_node->menu_order+1, $post_ref_node->post_parent, $post_node->ID ) ); |
Changing the plugin to reduce the score that is not necessarily tied to any true issue seems like a bad use of a developer’s time, so the whole scoring system seems problematic, especially when it is such a black box. Making this all the more problematic our previous run in with the results of this company left a lot to be desired.
A Truly Vulnerable Plugin Gets a Score of 0
To get better idea of the quality of the results we checked a plugin we know currently contains a vulnerability. The latest version of the plugin Advanced Contact form 7 DB introduced a vulnerability that while unlikely to be exploited on most websites using the plugin, would be very serious on some and could be used effectively in a targeted attack. The possibility of that vulnerability is something flagged by our own automated security checker for plugins and since the same check is used for our proactive monitoring of changes made to plugins to try to catch serious plugin vulnerabilities before they can be exploited we already ran across the issue and have notified the developer of the issue. Hopefully it will be fixed soon.
That plugin gets a RIPS CodeRisk score of 0 despite all of that:
Providing Clearer Results
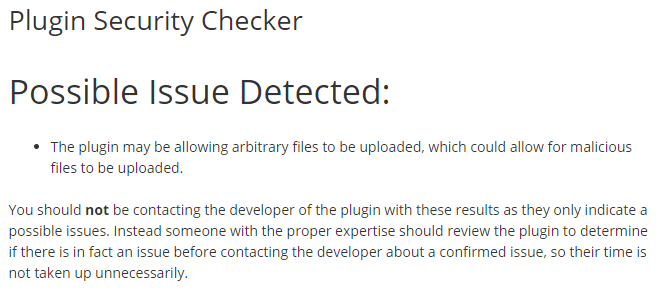
Our tool, the Plugin Security Checker, doesn’t provide a black box score like that tool does. Instead it provides information on any possible issues detected and for customers of our services the underlying code is provided to help a qualified individual to check to see if there is in fact a vulnerability in the code that the developer should be made aware of. As can be seen by the result for Advanced Contact form 7 DB we specifically recommend not contacting the developer just based on the result of the tool: