WPScan Vulnerability Database Includes Fake Vulnerability, Claims It Was Fixed
Last month there was report of a remote code execution vulnerability in the plugin Robo Gallery, as we discussed at the time the vulnerability didn’t actual exist (though another vulnerability did exist in the relevant code). Despite the fact that it didn’t exist and couldn’t possibly have been exploited as shown in the included proof of concept, that hasn’t stopped people from trying to exploit. We had one attempt on our website the week after the report and a recent thread on wordpress.org indicates that attempts are continuing to happen. Based on what request were sent in those two situations, those were done by different people, with the second one being from someone who was less aware of the problems with the advisory, considering they sent a GET request when that couldn’t possibly work.
While doing some more looking around on this we found it is not only hackers that didn’t bother to actually look at the vulnerability report. The fake vulnerability is also listed in the WPScan Vulnerability Database, which is a database of vulnerabilities related to WordPress. That database is used in a number of plugins for alerting to vulnerable plugins.
What is rather strange about the listing it states that “This is potentially a False Positive. Needs further investigation.”, while at the same time claiming that it has been fixed:
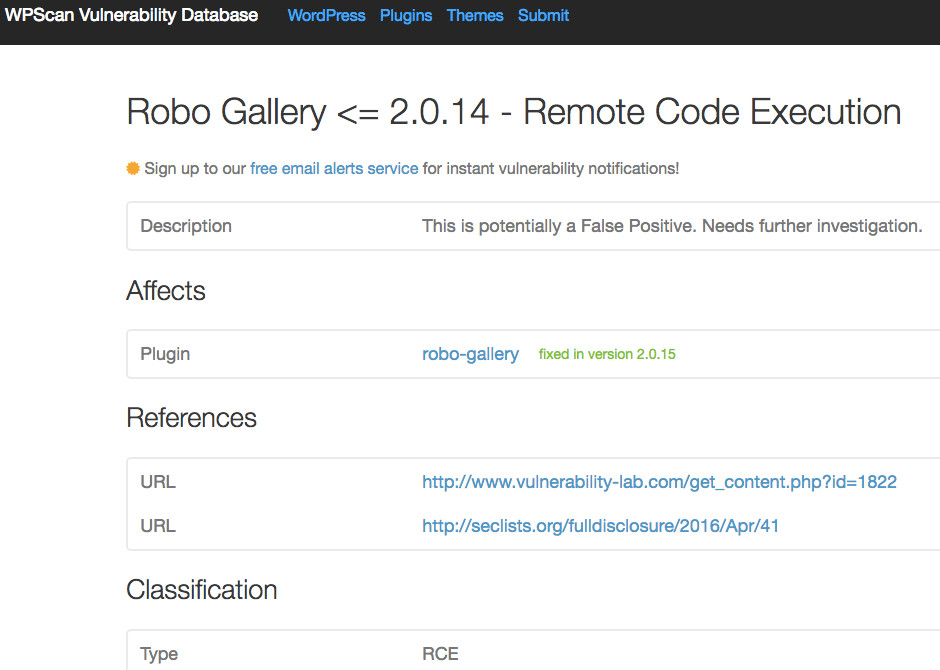
How they know it has been fixed, but not being sure if it actually exists in the first place, is curious at best.
What makes this more problematic is that it looks like many of the tools that use their data just display the title of the vulnerability, so the disclaimer in the description would not be shown.
This is great reminder of the importance of testing out vulnerabilities before including them in data sets of vulnerabilities, which we do, but others, including the WPScan Vulnerability Database don’t do. That lack of testing leads to other problems like the WPScan Vulnerability Database claiming that vulnerabilities that haven’t been fixed were in fact fixed, which leaves users of their data falsely believing they are secure against publicly disclosed vulnerabilities.