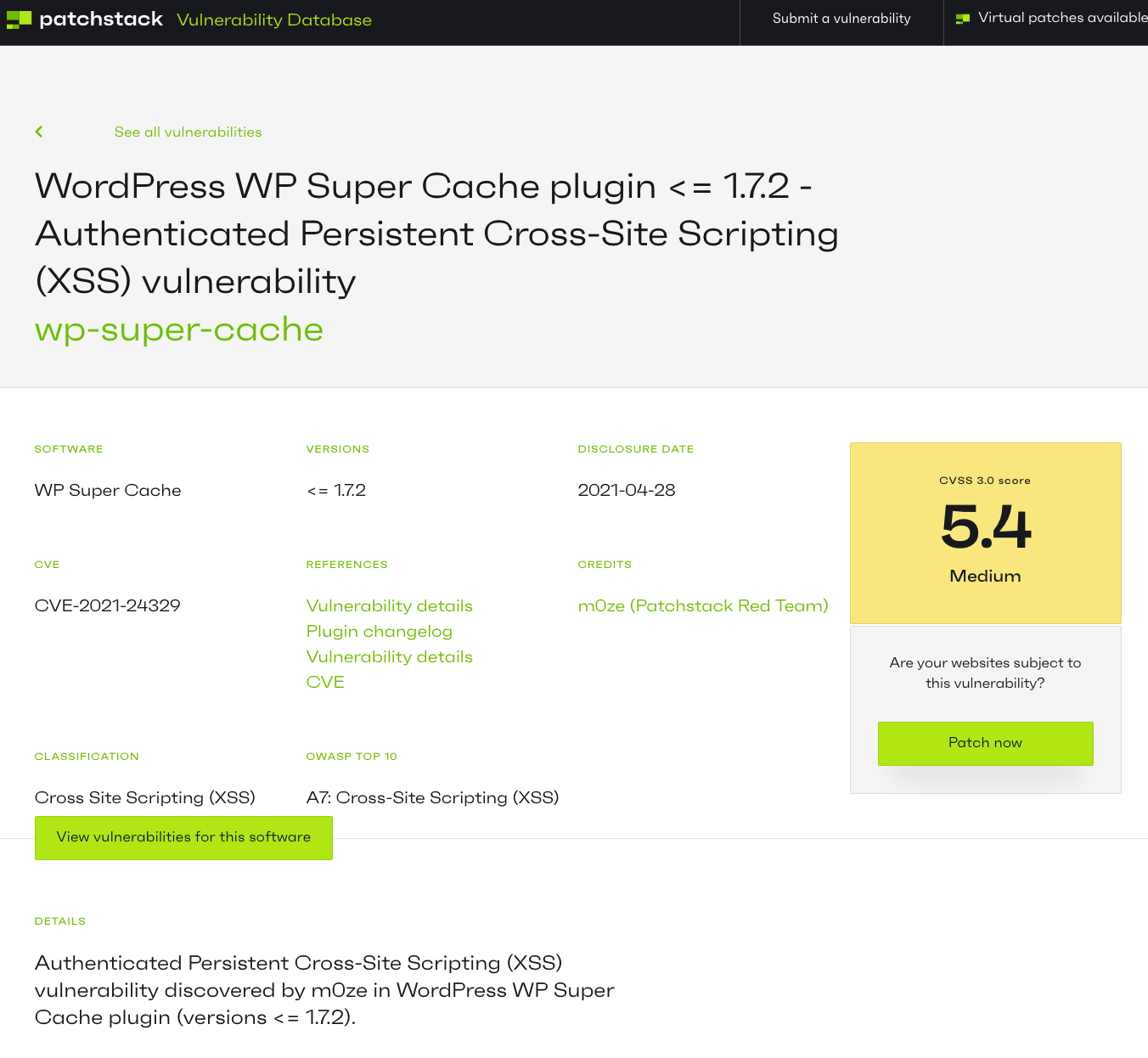
Cross-Site Request Forgery (CSRF)/Cross-Site Scripting (XSS) Vulnerability in Picture Gallery
A new report claims that there is a stored cross-site scripting (XSS) vulnerability in the WordPress plugin Picture Gallery. Like a lot of recent reports this isn’t really a vulnerability as the attacker would need to be logged in to WordPress as an Administrator to exploit this. But while confirming that was in fact the case, we found that there is actually a cross-site request forgery (CSRF)/cross-site scripting (XSS) vulnerability in somewhat related code in the plugin.
With the supposed vulnerability, it involves accessing a page only accessible to those with the manage_options capability, so Administrators: [Read more]