WordPress Hasn’t Addressed Hacker Targeted Plugin With 100,000+ Installs That Has Unfixed “Critical” Vulnerability
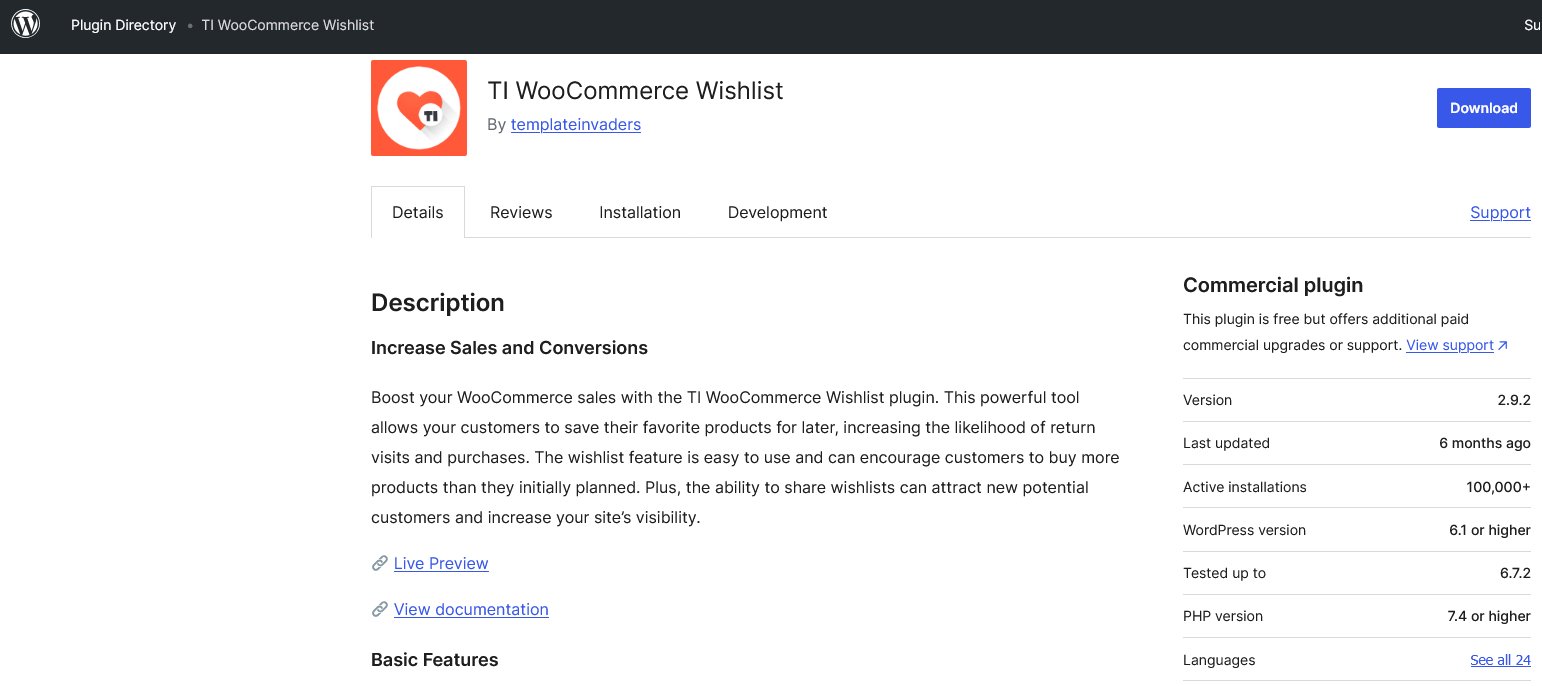
Yesterday, data we track showed that what was likely a hacker was probing for usage of the 100,000+ install WordPress plugin TI WooCommerce Wishlist, by requesting its readme.txt file. Why would a hacker be interested in the plugin? Presumably there shouldn’t be any publicly known unfixed vulnerabilities, as the plugin hasn’t been closed in the WordPress plugin directory: