Authenticated Open Redirect Vulnerability in Paid Memberships Pro
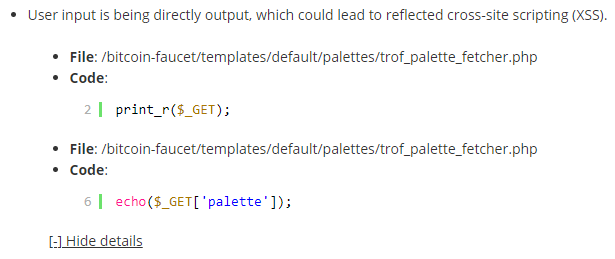
One ongoing indication of the poor security of WordPress plugins is how often our Plugin Security Checker, which is an automated tool for identifying some possible security issues with plugins, is picking up vulnerabilities in fairly popular plugins. We would not describe the tool as being advanced by any means, so that being true is not a great indication of the handling of plugins’ security. In looking over some of the recent results for plugins in the Plugin Directory that were checked through that to see if could further improve its results we found that the plugin Paid Memberships Pro, which has 80,000+ active installations according to wordpress.org, contains an authenticated open redirect vulnerability.
That is a type of vulnerability that isn’t really a concern in terms of being exploited on the average website, but it is something that looks like it could have easily been avoided. You can check the plugins you use to see if they are possibly impacted by a similar issue or a number of other issues through the tool for free. [Read more]