One of the problems we have found with the WordPress Support Forum is that there is unproductive and inconsistent deletion of claims about the security of plugins. In an instance from just a couple of days ago a thread was deleted which mentioned an unfixed vulnerability in the plugin File Manager, deleting that doesn’t make much sense to us since it would be easy for someone with bad intentions to do same monitoring that we do and have spotted that thread before it was deleted, while deleting makes it harder for those with good intentions to find out about it. For us seeing it, not only lead to us noticing a related vulnerability in the same code, but it also led to a new check for our Plugin Security Checker to make it easier for similar issues to the one we noticed to be caught and fixed going forward, leading to better security for WordPress plugins, which unfortunately the moderators of the WordPress Support Forum don’t seem to be all that interested in based on the actions they take and their shutting down any conversion about whether those actions are productive.
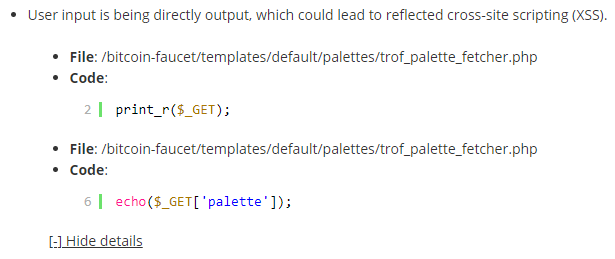
The additional vulnerability we noticed is a reflected cross-site scripting (XSS) vulnerability, which could possibly allows an attacker to run arbitrary malicious JavaScript code. This type of vulnerability isn’t a big threat since it requires getting someone else to take an action, which we don’t see hackers really interested in when it comes to untargeted attacks, and web browsers other than Firefox include filtering to restrict the ability for this type of vulnerability to be exploited. [Read more]