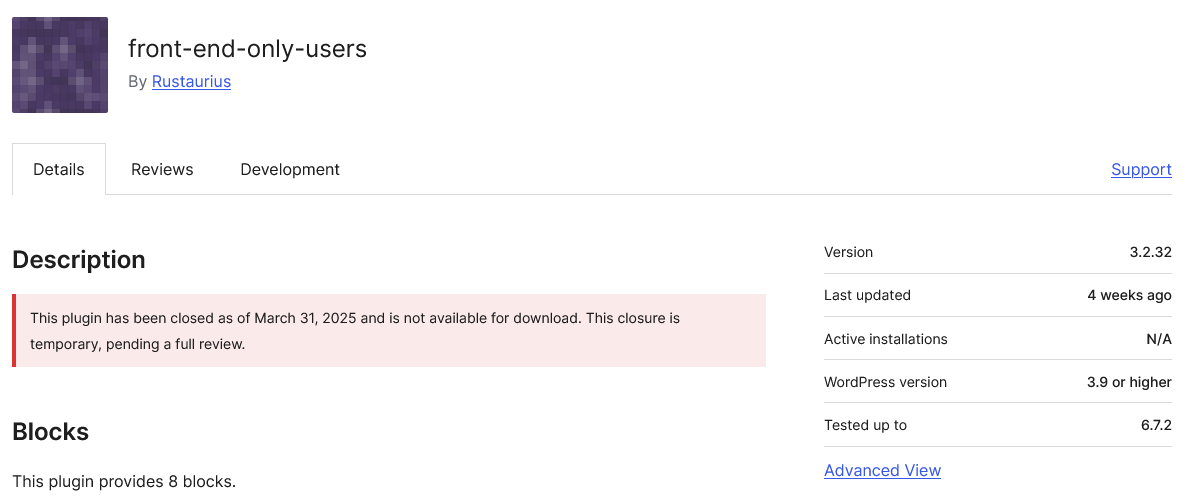
Actual Accident Leads to Unfixed Vulnerability Hacker is Likely Trying to Exploit in WordPress Plugin
On Friday we looked at a vulnerability likely being exploited in a WordPress plugin, where there is a fix, but WordPress hasn’t made it available. Like that situation, we had what appears to be a hacker probing for usage of the plugin Front End Users over the weekend by requesting the readme.txt file for the plugin. Like that previous situation, the plugin is closed on the WordPress plugin directory: