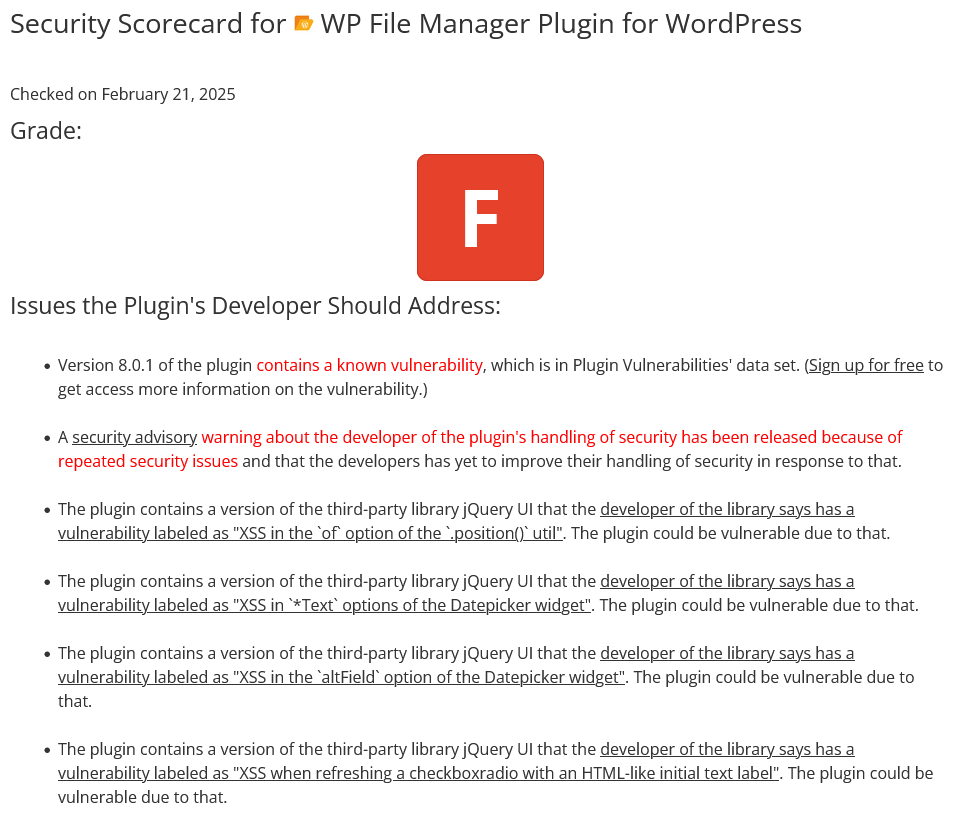
Developer of 1+ Million Install WordPress Plugin Warned Multiple Times of Known Vulnerable Library in Plugin and Still Hasn’t Addressed It
Yesterday, we covered our finding that the 1+ million install WordPress plugin WP File Manager contains a known vulnerable version of the JavaScript library jQuery UI. While following up on another element of that situation, we ran across the developer of the library having been warned publicly about that twice in the past. The developer responded both times that they would address it and then didn’t. That also means that they knew about the problem with another library and didn’t warn the developer of it.
The first notification was in April 2023 and the response from the developer then was: [Read more]