The Security and Vulnerability Shield Plugin Isn’t Getting New Vulnerability Data
As we look at how we can improve our service, one of things we are doing is comparing our service to other available options that provide a similar functionality. One such option is a WordPress plugin named Security and Vulnerability Shield. Looking at the information on its Plugin Directory page certainly makes it sound impressive, they claim to monitor numerous sources to collect their vulnerability data (emphasis theirs):
No need to monitor 20 websites and receive 100+ emails (from groups and newsletters) so that you can keep up to date with the latest vulnerabilities in WordPress and its related plugins… our team will do that for you!
They also claim they spend “tons of hours” collecting the data:
please remember that this is a free plugin and despite that it costs us tons of hours (of processing emails, data, reviewing plugins, exploits/vulnerabilities, developing and maintaining this plugin) we will try to always have a free version that helps the WordPress community to protect their sites.
You would certainly have to spend a lot of time to have launched the plugin with data on “3000+ known vulnerabilities and exploits”, as they claimed to have done.
Whomever is behind this also sounds impressive as they claim to have tested the plugin “on private client installations of more then 200 WordPress sites”.
Who Is The Developer?
But looking at the website of the developer, SiteCops, things start to seem less impressive. Currently their website just contains the word “home” as can been seen in this screenshot:

Looking at archive.org’s records shows that the website has been that way since at least January and they don’t have any records of actually content being on the website in recent years.
If you are spending all this time of the service, you would think that your website would have some basic details at least.
We then went looking for any other information available the developer. Their domain name’s whois information just list a company that hides the true registrant. A Google search didn’t pull up anything on them.
Along with several things we noticed after that, we started to wonder if the developer was really doing the work they claimed or possibly taking data from someone else and claiming it as their own. We did some basic checking on that, but we couldn’t get very far in determining if that was case, due to the limited amount of information they provide about vulnerabilities. They don’t list the type of vulnerability or provide the web address with details the vulnerability, which would likely allow fingerprinting the actual source if it was copied from somewhere else. The limited nature of the vulnerability data also makes the service’s value limited, since the impact of a vulnerability varies widely from one vulnerability type to another.
No Data on Recent Vulnerabilities
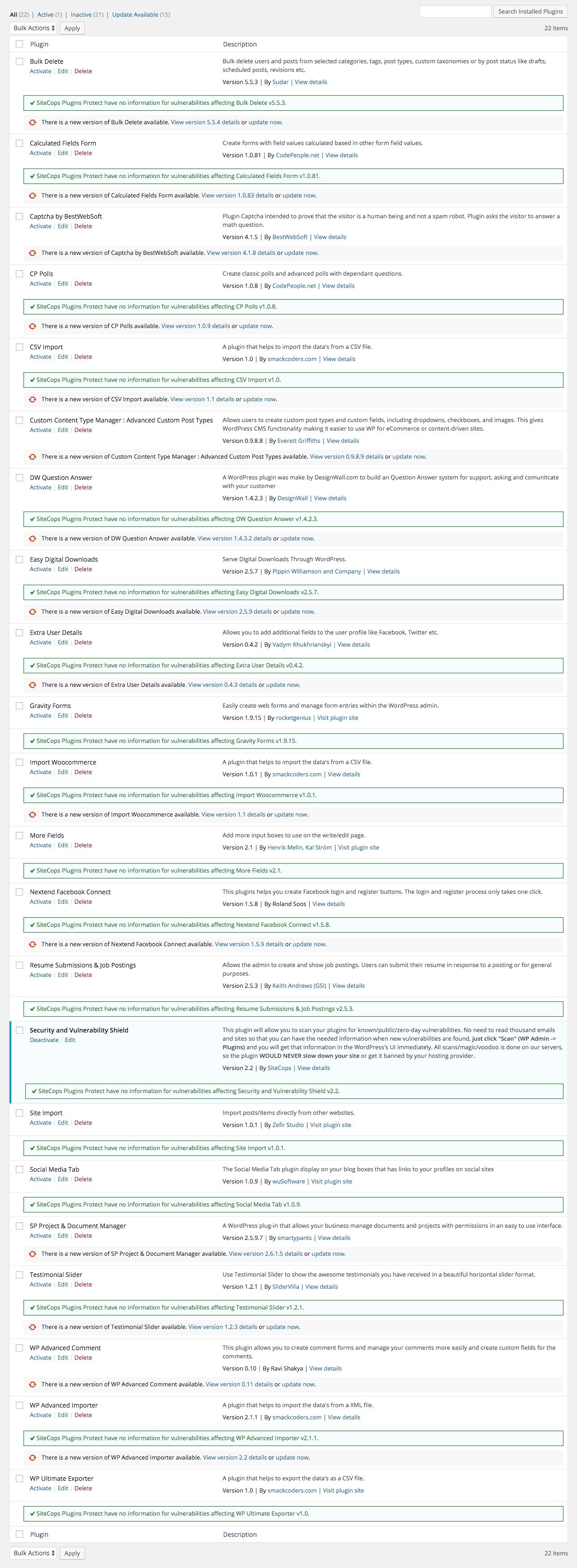
The next thing we wanted to see is how the service stacked up to our service in terms of adding new vulnerabilities. Since their website doesn’t have any information on recently added vulnerabilities we thought a good starting point was to see how many of the new vulnerabilities we had added to our data in the last month were included in their service. It turned out that they had none of them. You can see in this screenshot they don’t report vulnerabilities in any of the plugins, despite all of them containing vulnerabilities in the installed versions (excluding the Security and Vulnerability Shield plugin):
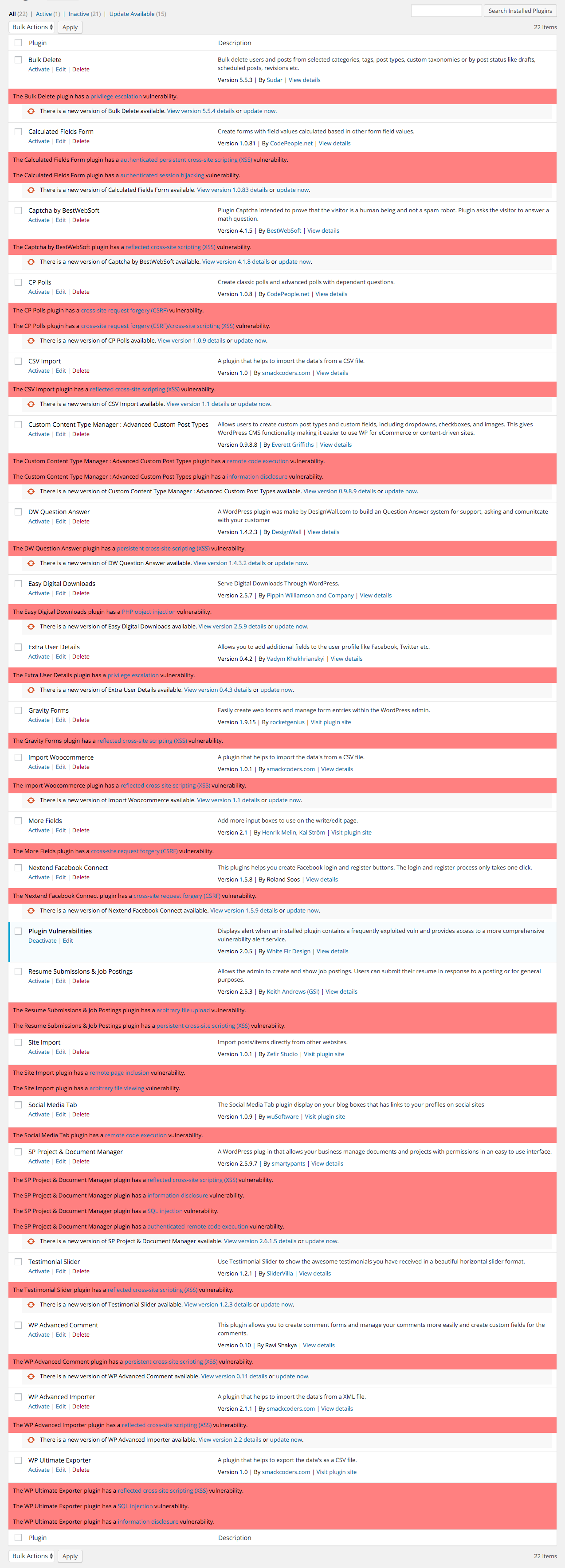
By comparison you can see we have at least one vulnerability listed for each of the plugins (excluding our own plugin):
So if you are looking to be warned about vulnerabilities in WordPress plugins, this plugin doesn’t seem to be a good option at this point.
Thanks again for the time spent on testing our plugin.
However, it is a bit misleading to just say: “Hey, you don’t have data for those X plugins”.
The importance and the value of our plugin (and dataset) can’t be measured by just checking X plugins.
Last, but not least. This behaviour (randomly posting “this does not work! stop using it!” for 3rd party plugins and sites (from what we’d seen by simply googling “White Fir Design”) that are a competition to your plugins and services with the idea to advertise your own product is a very, very, very childish, misleading for the users and unprofessional.
Thanks,
SC Team
We didn’t say “Hey, you don’t have data for those X plugins”, we provided evidence that your dataset is not being updated anymore, which you have already acknowledge was true.
As for your statement that “The importance and the value of our plugin (and dataset) can’t be measured by just checking X plugins.”, doesn’t match up with what else you are saying. The description of your plugin is “This plugin will scan your plugins (and WordPress) version for more then 3000+ known vulnerabilities and exploits.”. Your explanation for why you were not updating your dataset also was based on numbers, “Our goal is to double the number of vulnerable plugins data that we’d captured…however, as mentioned on our plugins info page – for a *FREE* plugin, this is a major effort and that’s why we had delayed the delivery of the new set of data and our newest versions.”. So you clearly are making it about numbers, while we didn’t.
Though we do want to warn the users of our service about as many known vulnerabilities in their plugin as possible, the focus of our service is not just about listing the most vulnerabilities, it is about improving the security of WordPress plugins. For example, we test out each vulnerability we add to our dataset, which means we often find that vulnerabilities have not actually been fixed and make sure they do actually get fixed (including when the people running the Plugin Directory have failed to notice that). That helps everyone, even if they don’t use our free plugin or our service.