Is Poor Documentation To Blame For Some of The Security Vulnerabilities Related to WordPress’ AJAX Functionality?
One of the frequent causes of vulnerabilities being disclosed in WordPress plugins these days involves in part functions that are made available through WordPress’ AJAX functionality that don’t have the proper restrictions on who can access them. In many instances this involves functions that are made available to anyone logged in, despite only being intended for high level users. In the other instances, there is the more serious problem of these function being made available to anyone, including those that are not logged in. Seeing as many websites don’t allow untrusted individuals access to an account, a vulnerable function being accessible to those not logged in greatly increases the chances of it being exploited.
One big difference between these two issues is that to make the function accessible to those logged out the developer has to specify that they want them to have access, while a lack of restrictions on which logged in users can access the function is the default state. That raises the question as to what leads developers to provide access to those who are not logged in, when that isn’t needed.
The answer in part looks like it could be due to the some of the WordPress documentation.
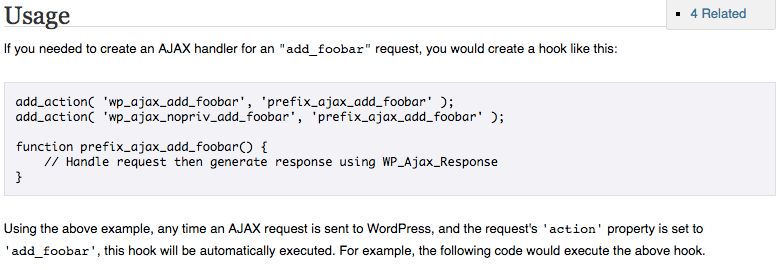
Currently for us doing a Google search for “wp_ajax” brings us the WordPress codex page Plugin API/Action Reference/wp ajax (action) as the first result. It shows an example of setting up making an AJAX accessible function with it available to those both logged in and logged out:
No where on the page is any explanation of the two different hooks in the example do or anyone mention that this makes it available to anyone.
By comparison the second result, another codex page, AJAX in Plugins, only shows the hook for logged out users, wp_ajax_nopriv_, in a section on the “Viewer-Facing Side” and explicitly mentions that it would make available to those not logged in.
This seems like a good reminder that even documentation can play a role in security.
I’ve often thought that it would help if the Ajax system was more secure-by-default. But even if it was, if the documentation gave examples of circumventing that without proper explanation about what was going on, I guess we’d be little better off than we are now.
One good thing is that the anybody who is inclined to improve that codex page could, because the codex is a wiki. (Although on the downside this can also result in bad examples being added in the first place.)