Other WordPress Plugin Vulnerability Data Sources Still Not Warning About Fixed or Unfixed Vulnerabilities in Easy WP SMTP
Today we have had a lot of traffic coming to our website to our posts about the vulnerabilities fixed and unfixed in the plugin Easy WP SMTP. The likely explanation is what else we have been seeing today, as in terms of dealing with the cleanup of hacked WordPress websites over at our main business and other mentions of hacked websites, we are seeing indications that the option update vulnerability that was fixed with that and possibly the other recently fixed option update vulnerability impacting many plugins are being exploited widely to change the WordPress option “siteurl” on websites to cause requests to be made to “getmyfreetraffic.com” (based on past experience with this type of vulnerability that likely isn’t the only thing the hackers are doing with the vulnerabilities on those websites).
Customers of our service using that plugin have already been warned about the fixed and unfixed vulnerabilities in that plugin, but for anyone relying on other data sources for info on vulnerabilities in plugins they use, they are so far in the dark.
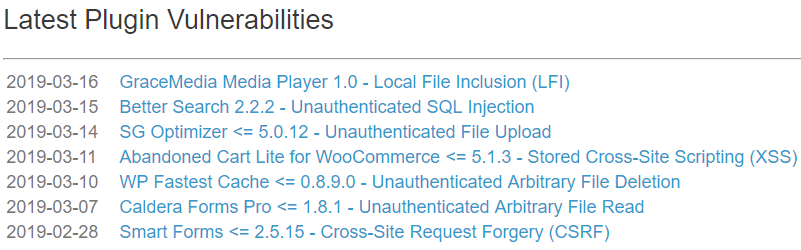
Here for example are latest plugin vulnerabilities added to the data of WPScan Vulnerability Database:
That data source is widely used by various plugins and services, though often without disclosing it is the source.
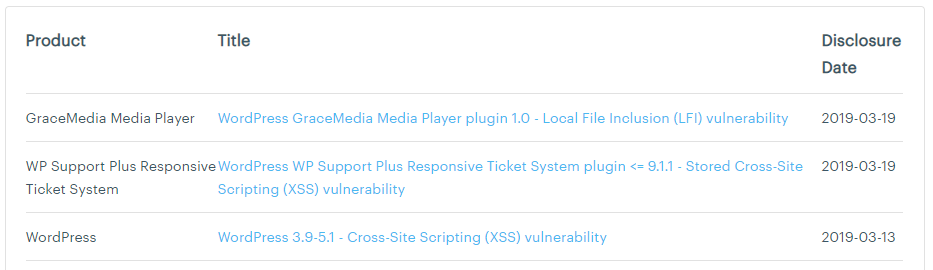
And ThreatPress (which seems to consist mainly of data copied from WPScan):
If you keep your plugins up to date at all times as we recommend and created a plugin to assist in doing, then the impact of being in the dark would be limited since the vulnerability being exploited has been fixed already, but many people don’t follow that advice.
For example, we once ran across someone relying on email sent by the Wordfence Security plugin, which relies on WPScan’s data, to determine when to update plugins:
We maintain a large client base and rely on these emails to quickly determine if the update needs to be applied immediately (Security related) or if it can be put on hold temporarily (Feature update).
Amazingly Wordfence didn’t discourage that behavior despite that they should know how dangerous it is, instead one of their employees responded to that person by lying about the quality of their data.
Now is as good a time as ever time to sign up for our service. If you have a WordPress website that needs to cleaned you can get a free lifetime subscription while getting a proper cleanup (while other providers won’t even properly clean up the website).