WordPress Plugin Developers and Users Should Be Proactive, Not Reactive, About the Security of Them
This week the WordPress plugins Easy WP SMTP and Social Warfare had vulnerabilities, which have now been fixed, widely exploited. In both cases the vulnerabilities were not due to obscure issues that no one had ever heard of before, but they were due to the failure to do security basics. In the case of both plugins, even after having vulnerabilities exploited, the developers still haven’t fully fixed up the security of the code related the vulnerabilities (and the WordPress team has allowed them to remain in the Plugin Directory despite that).
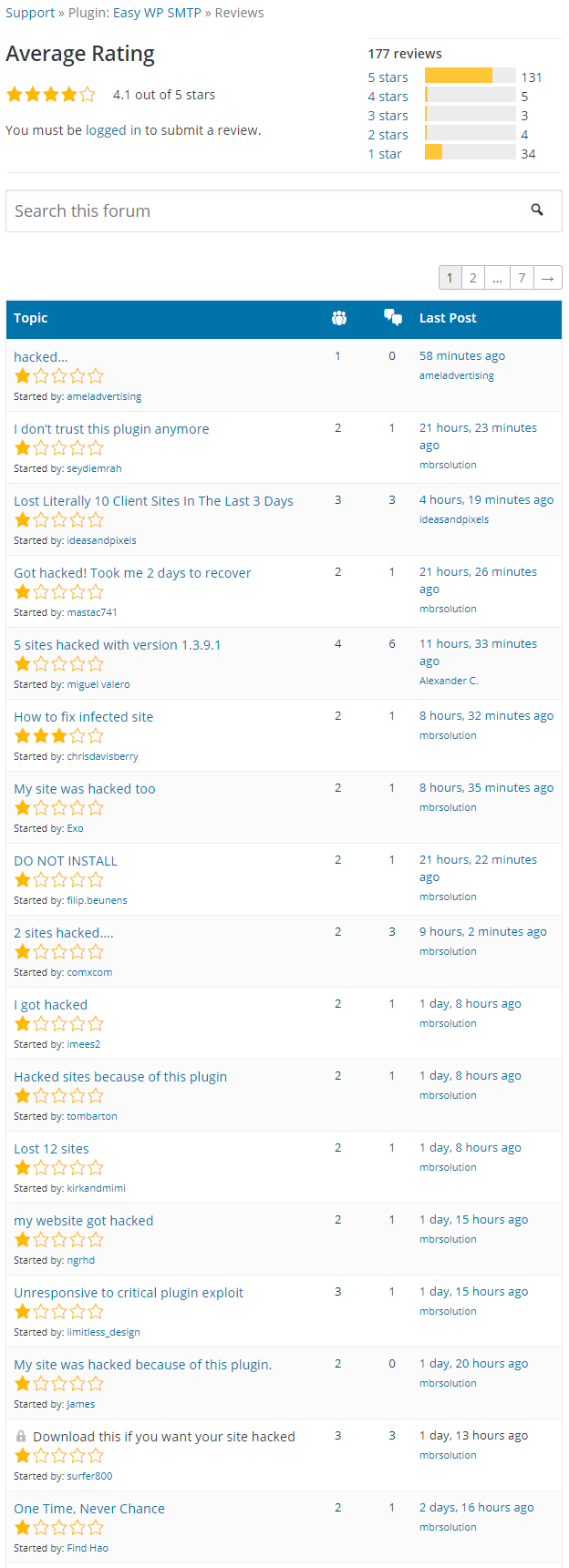
Both plugins have started picking up quite a few negative reviews since the exploitation.
Here are the latest reviews for Easy WP SMTP:
And for Social Warfare:
What seems like the obvious takeaway from that is that developers should focus more on the security of their plugins, especially in the case a plugin like, Social Warfare, where there is a paid version, so they would be better able to hire us or someone else to do a security review of the plugin. But maybe what is better to focus on is the users of the plugins and their need to think more about the security of the plugins they use before the worst happens instead of after.
Some of the reviews don’t necessarily indicate they are thinking of things in that way. Here is one review of Easy WP SMTP with the title “I don’t trust this plugin anymore“:
This plugin opened the back door to the hackers. My many web sites hacked by this backdoor. I never use this plugin
Not trusting a plugin after it has been exploited doesn’t seem like the greatest idea, since you could just be moving to another plugin that is insecure itself, but that hasn’t led to a mass exploitation yet. A better reason to stop using would be that there are still less serious vulnerabilities in it that haven’t been fixed.
What would be better is to determine if the plugins is properly secured before running into a problem. Other reviews have people claiming to have a lost money, time, and client goodwill due to this, if they had spent money our service, which allows customers to suggest/vote for plugins to get a security review, or hired us to do a security review they could have spent money in a way that help them avoid this situation instead of deal with after effects and helped others as well (how much it would help others would depend on if the developers properly secured the plugin after getting the results of the review).