WebARX Hides That Their Firewall Failed To Provide Same Protection Simply Updating WordPress Plugin Would Have
Yesterday a company named WebARX discussed a vulnerability we had discovered in a WordPress plugin named Social Warfare, though you wouldn’t know that it you read their post:
Last week, an unnamed security researcher publicly disclosed security vulnerabilities in the popular WordPress plugin “Social Warfare“.
Why not properly credit us there? Well one explanation is that they wanted to promote themselves without dealing with the fact that they actually provide a service that provides worse protection then simply keeping your plugins up to date.
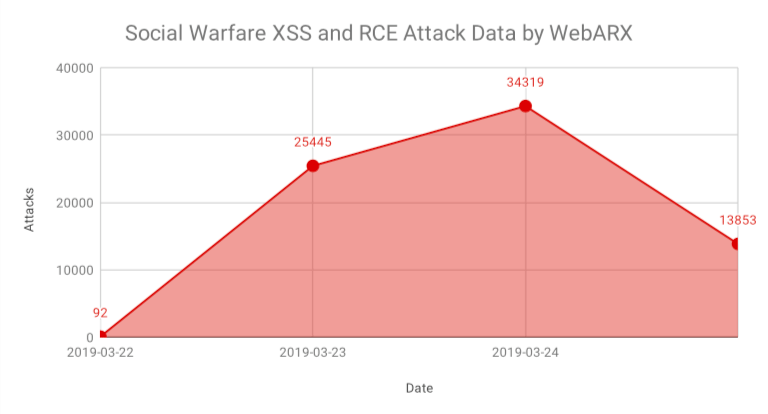
We disclosed that vulnerability on the 21st and it was fixed the same day. It was getting exploited that same day. None of that is mentioned in WebARX’s post. Instead they have this chart showing that hacks started the next day (and barely started at that):
In the conclusion of their post they write this:
We strongly encourage you to update Social Warfare plugin to the latest version (3.5.3). It patches both vulnerabilities mentioned in this article.
Firewall rules for both of those vulnerabilities have been shipped to WebARX users since 22nd of March.
Considering that post was released yesterday, the advice to update the plugin is way behind. What the advice should have been is to keep your plugins up to date at all times, since that would have provided you protection on the 21st, which was a day before they claim to have added protection.
What then might explain the chart is that they are only detecting hacking attempt after they have added protection, which means something like that is of limited value.
If you actually want to improve the security of WordPress websites beyond keeping plugins up to date, getting plugins security reviewed would actually do that.
Your disclosure was released on 21st, the 22nd March started in our (WebARX) timezone (London) around 3PM 21st in Colorado US (where you’re based).
We will add the credit(source) to the XSS discovery in our blog.
Additionally, we do notify out customers via email and slack integration about the vulnerable plugins on their sites. We actively propagate the critical importance of updating plugins, themes and WordPress core among our users.
We are familiar with how time zones work and how that might have impacted things, but both our post and the fix for the vulnerability were released on the 21st in your time zone as well as ours. Also, when it was Midnight in London, it is 6pm in Colorado, not 3pm.
After doing some more research and checking out their blog and email, I think it is time to switch to a better security plugin too. In this web environment that is full of vulnerability everyday, it’s better to use a security solution that is reliable and provides solutions, not explanations on why they lacked.