WebARX’s Idea of Threat Intelligence Involves Copying From the Low Quality Data of the WPScan Vulnerability Database
The phrase “threat intelligence” seems like it is becoming popular among security companies that are more focused on BSing than doing the work that threat intelligence would entail, with the results for their customers being poor (up to their customers getting unnecessarily hacked). We recently ran across a post from WebARX, which we will get to the details of in a second, but at the end of was this claim:
Threat intelligence and prevention is our main focus and thus our firewall engine is updated on a daily basis.
That is undermined by what is written a couple of paragraphs up:
It can take just days from a disclosed plugin vulnerability to a full-scale attack campaign. Attacks in this nature are almost always automated. To be able to fight back, you have a small time window to take action. In such cases, web application firewalls have critical importance.
Not only are vulnerabilities frequently being exploited before being disclosed, which they would know if they were really doing what threat intelligence would involve, but as we noted with WebARX in the past, with the type of firewall protection they are focused on, the protection is often too late.
The post in question was about WordPress plugin vulnerabilities from the last week, though what really showed through was that seem to have little understanding of what they are dealing with.
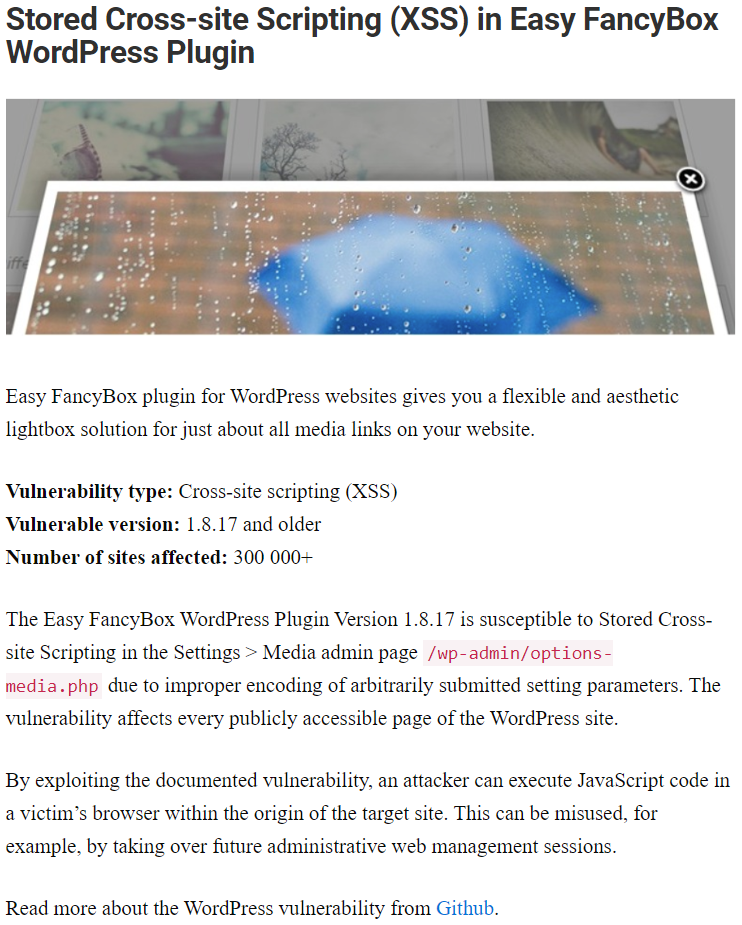
For example, with one those they noted that a vulnerability had been fixed, but if you even did quick glance at things, as we did, it was obvious that the issue hadn’t been properly resolved:
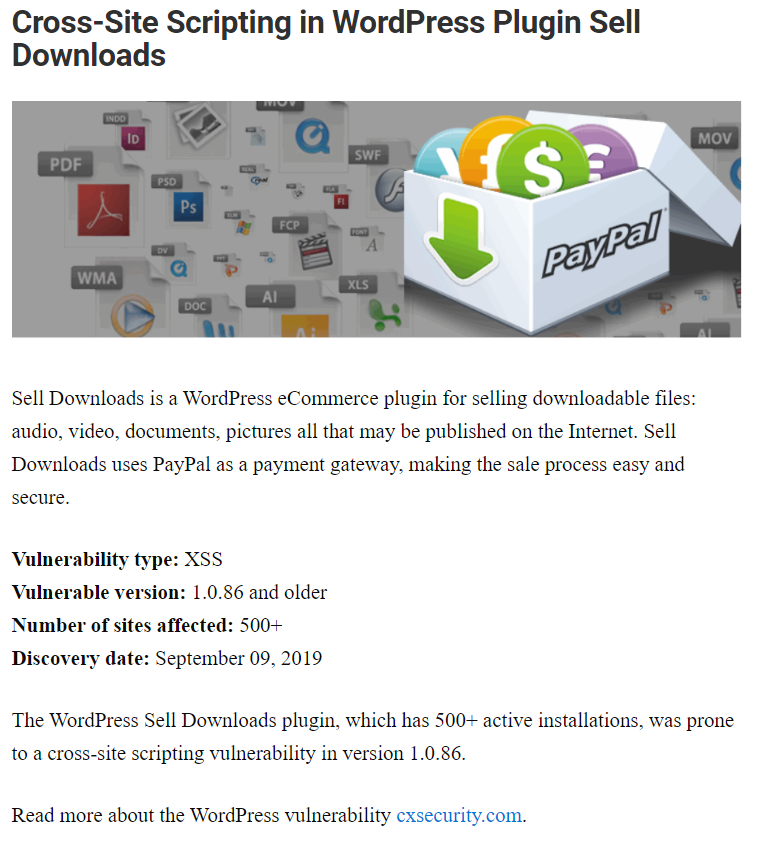
With another claimed vulnerability there wasn’t even a vulnerability:
In fact that happened twice:
What stood out overall is that what they appear to be doing is following the data coming the WPScan Vulnerability Database, which someone that really does threat intelligence would know of is quite low quality. Both in the quantity of vulnerabilities being added and the quality of their data.
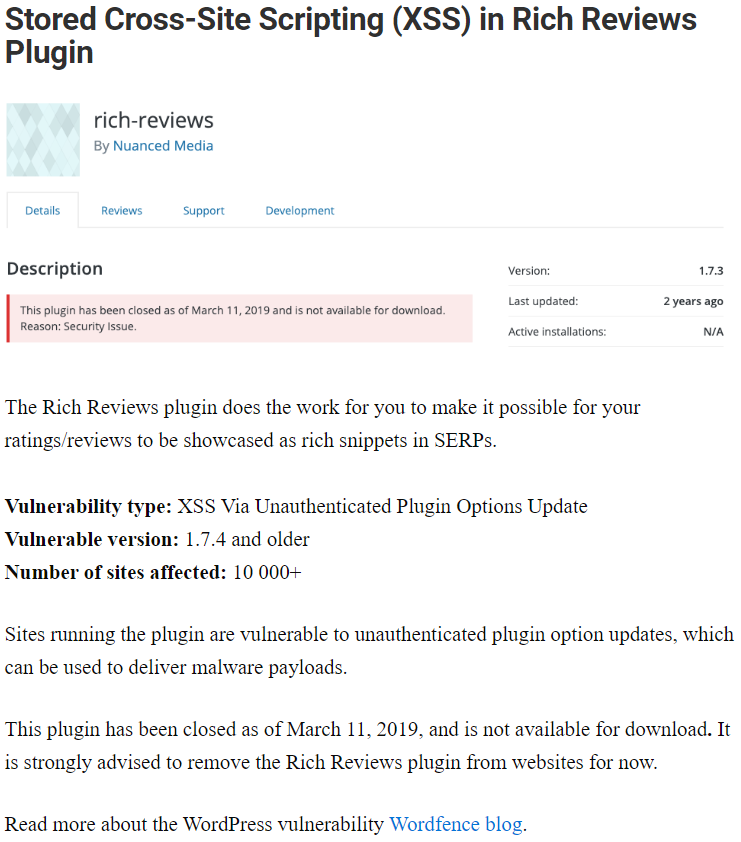
That is produces poor results, like thinking that a vulnerability we disclosed in December of 2017 was disclosed last week:
And not being aware of a widely exploited vulnerability that we had warned about a couple of weeks ago and that we noted freshly last week was confirmed to being exploited. The title of the later linked post, Exploitation of Vulnerability in Simple Fields WordPress Plugin Shows That Unlike Other Security Providers We Keep Ahead of Hackers, seems further confirmed by WebARX’s post.

Webarx threat intelligence can’t secure their own app!!
https://www.acunetix.com/vulnerabilities/web/wordpress-plugin-webarx-cross-site-scripting-1-3-0/