WPScan and Patchstack Spread False WordPress Plugin Vulnerability Report That Looks Like Satire of False Report
One of the things we provide to customers of our service as part of our data set on WordPress plugin vulnerabilities is information on false reports of vulnerabilities. These days the source of many of those false reports is not who you would expect, as it is the two main other data providers. One of those, WPScan, claims that they are verifying these false reports and the other, PatchStack, is claiming to be providing patches for them. In both cases, what they claim to do flies in the face of them spreading obvious false reports. One of those reports is so bad it reads like it would be someone in the industry attempt at satirizing bad reports, not something being claimed to be real.
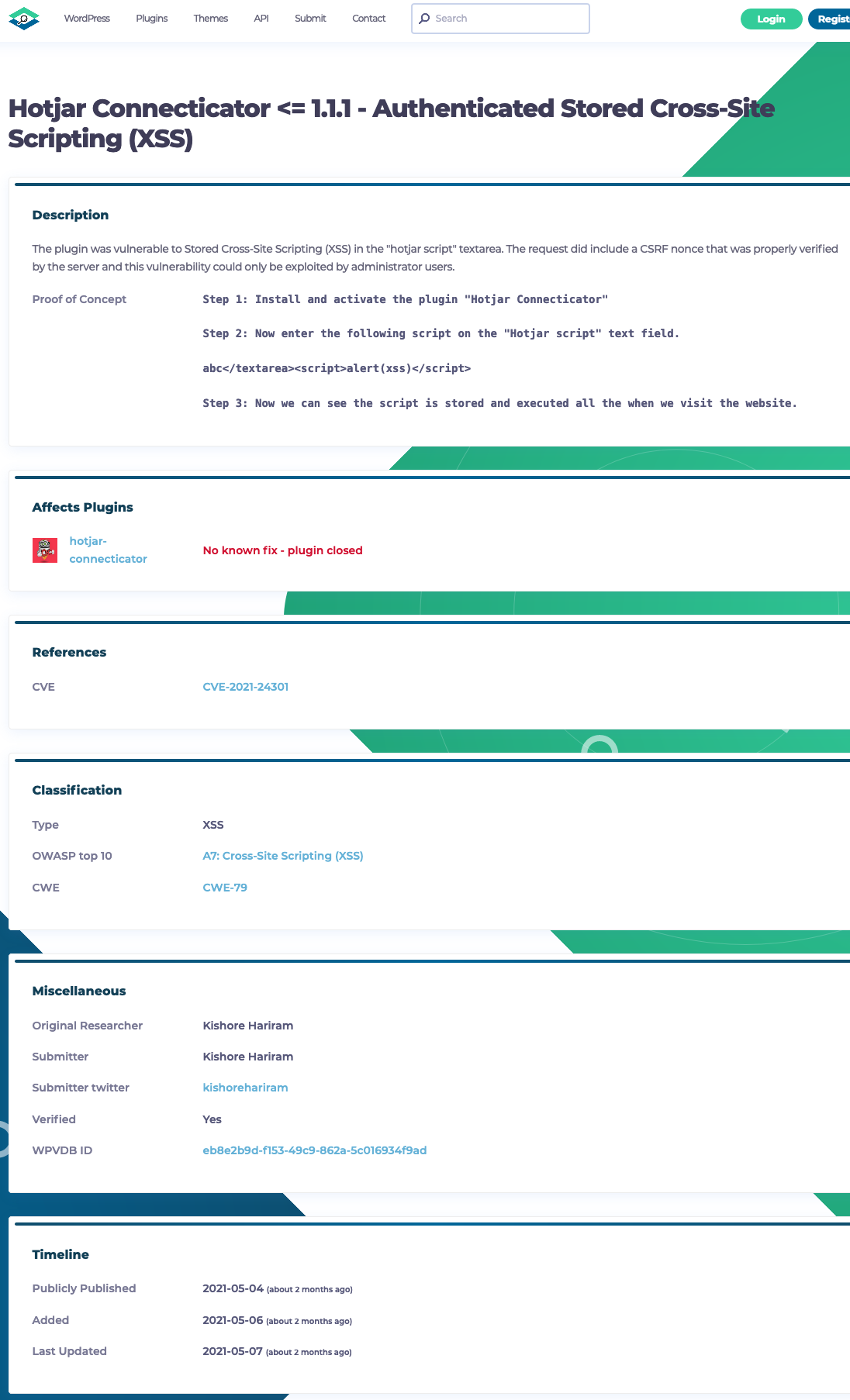
The report involves a plugin named Hotjar Connecticator, which was removed from the WordPress plugin directory at the time this report was released. The report was published directly with WPScan:
The first part of the description there is:
The plugin was vulnerable to Stored Cross-Site Scripting (XSS) in the “hotjar script” textarea.
While that is written in the past tense, confusingly, again, they claim the vulnerability hasn’t been fixed:
No known fix
The rest of the description is a head scratcher:
The request did include a CSRF nonce that was properly verified by the server and this vulnerability could only be exploited by administrator users.
So the claim is that someone logged in to WordPress with the ability to do anything, since they are an Administrator, would have to intentionally do this. That isn’t a vulnerability and it shouldn’t take a security expert to understand that. Among many issues with this, an Administrator could remove security code from a plugin.
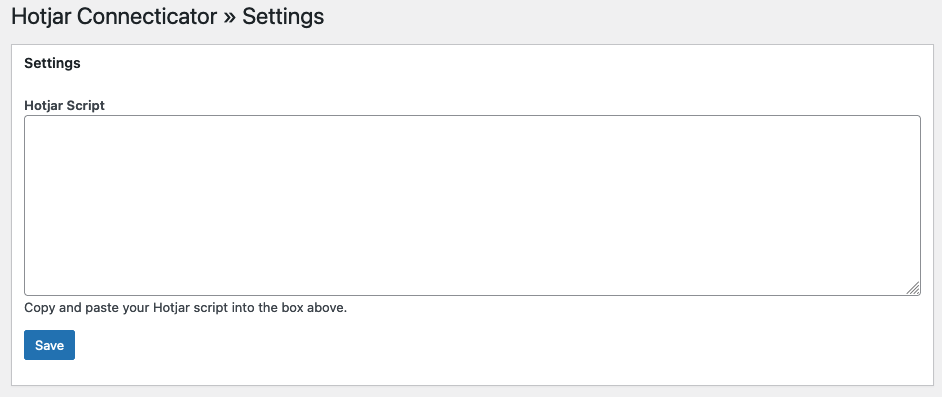
But things get worse from there, as the setting here is explicitly supposed to store JavaScript code, which is what stored cross-site scripting involves:
Would it be better to have the setting output on its setting page in escaped form, sure, but that doesn’t make it a vulnerability.
Patchstack Too
Patchstack looks to largely copy their data from WPScan, without bothering to filter out stuff like this:
In this case, without providing any credit, as the only reference listed is to “Plugin changelog“, which is actually just to main page for the plugin on WordPress plugin directory and doesn’t make any mention of this security vulnerability (it didn’t mention security at all until long after they posted that).
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade

Guys, have you noticed that it is about CSRF “Cross site request forgery”. It means that and wp admin can visit a malicious website and this website can use the wordpress login cookies to add this javascript to the hotjar.
That would be quite bad as Admin won’t know anything about this.
I would remove this article being you 🙂
We didn’t notice that, because that isn’t true. We even quoted WPScan saying that there wasn’t an issue with CSRF: