Wordfence’s Explanation for Misusing the Term Brute Force Attack is Something
While working on another blog post explaining how Wordfence inflates the number of “attacks” that their plugin blocks, we ran across a rather stunning explanation as to why they are misleading people about the type of attacks are concurring against WordPress admin passwords.
Attempts by attackers to log in to WordPress is not something that the administrators of the average WordPress needs to worry about. All they need to do is to use a strong and unique password and then they can move on to other things. That is bad for the security industry, as WordPress already provides a password strength meter. That might explain why they mislead people about what is happening, telling them that brute force attacks are happening and then recommending plugins and other solutions needed if those were really occurring (so this isn’t a semantics issue). Not only does that does that waste time and create unnecessary fear, it has led to websites becoming vulnerable, as plugins to handle brute force attacks can and have introduced security vulnerabilities on websites. This is the security industry at its worst, but they are able to get away with it.
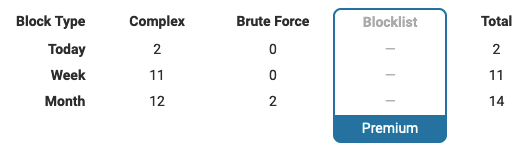
The Wordfence Security plugin is part of the problem with that, as its dashboard shows a count of login attempts they have blocked as “Brute Force Attacks”:
In a recent report they put out (alongside another security company, WPScan), which is filled with inaccurate information, it gives this curious explanation of their misuse of the term:
More frequently, the term “brute force attack” describes a variety of password attacks. However, this is just another method threat actors use but it is more time consuming and resource intensive. Therefore it is less commonly used. This attack relies on random guessing of a password using a mix of characters, letters, and numbers to try and obtain a password and can take significantly longer to crack a password than the dictionary and credential stuffing attacks.
So what, because those attacks are uncommon, that makes it okay to misuse the term, causing it to seem to be more popular?
The other problem with this explanation is that the companies don’t seem to have a basic understanding of these types of attacks. With both dictionary attacks and what they refer to as “credential stuffing attacks“, they usually fail. A brute force attack will eventually succeed as the attack keeps trying passwords until it guesses the right one (this assumes the username exists). So saying that this type of attack “can take significantly longer to crack a password than the dictionary and credential stuffing attacks” isn’t accurate, as the other two types usually won’t succeed at all, so they won’t “crack a password” at all.