The Most Popular WordPress Security Plugin is Insecurely Using the extract() Function
Last month we noted that one of the largest companies in the WordPress ecosystem, Automattic, had a security team that didn’t seem to have a good grasp of a security issue they were publicly discussing. It turns out the situation is worse than we originally knew.
On the blog of Automattic’s Jetpack service, one of their security employees wrote a post seemingly oblivious that code he was discussing was doing something in a way that explicitly noted in the PHP documentation as something you shouldn’t do. Specifically, the documentation for the extract() function has this warning:
WARNING Do not use extract() on untrusted data, like user input (e.g. $_GET, $_FILES).
The WordPress coding standards go farther and say don’t use that function at all.
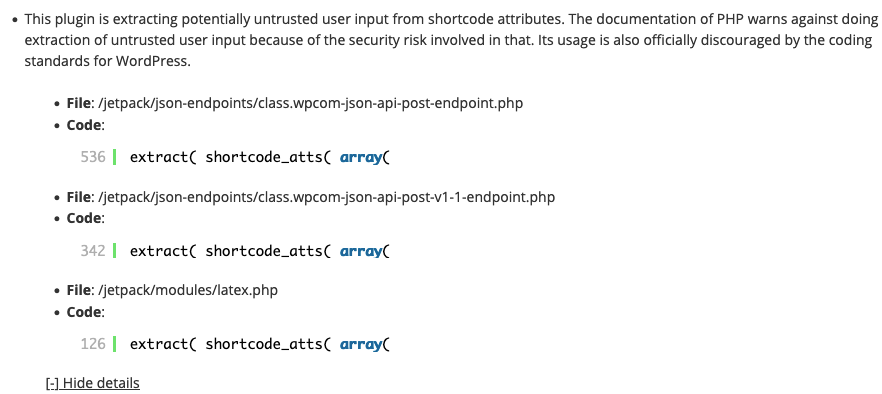
The code being discussed in that post took user input in the form of shortcode attributes and passed it through that function. As we noted in our post, the plugin being discussed in Jetpack’s post was still doing that, as many plugins do, despite it being something that shouldn’t be happening.
We contacted Automattic last month suggesting they could help to address the larger usage here since their employees apparently make up a large portion of the WordPress security team, so they could help push the team running the WordPress Plugin Directory to address this. We haven’t heard back from them. That makes this claim in their post seem hollow:
At Jetpack we work hard to make sure your websites are protected from these types of vulnerabilities.
As we noted in that post, our Plugin Security Checker tool will flag a lot of instances of that type of issue. We recently reopened access to tool to those not using our service and while reviewing the results of plugins from the WordPress Plugin Directory being checked, we noticed that one of the plugins checked, the most popular WordPress security plugin, contains multiple instances of that issue:
That plugin being Jetpack, which is first and foremost marketed as a security plugin these days:
That the most popular security plugin is not properly secured seems like a pretty good encapsulation of why WordPress security is in such bad shape.
If Automattic gets an interest in security, we love to work with them to fix the kinds of issues they are now part of the problem instead of part of the solution. Or help them to make sure their plugins are bettered secured with security reviews of them.