WPScan Claims a Vulnerability Was Fixed in Version of WordPress Plugin That Doesn’t Exist
One of the many problems that plagues security is the lack of concern with the truth from so many people involved in it. You would think that wouldn’t be the case with trust being an important part of security, but that is the case, hence security being in such bad shape. That is common when it comes to information on vulnerabilities in WordPress plugins, where we find that critical information, including if vulnerabilities have actually been fixed, is often inaccurate. While there understandable mistakes, that clearly isn’t an explanation for most it. Take something we noticed with one company that clearly isn’t interested in accuracy, WPScan.
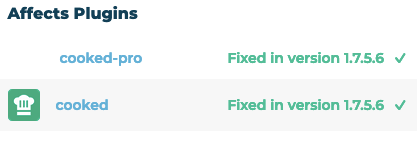
Yesterday we discussed looking in to why a hacker might be targeting a commercial WordPress plugin Cooked Pro. While looking in to that, we came across a WPScan entry that claimed a vulnerability had been fixed in the related free Cooked plugin in version 1.7.5.6:
The cited source for that entry made no claim that there even was a vulnerability in Cooked, just Cooked Pro.
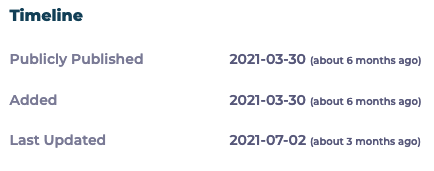
WPScan’s entry is listed as being added on March 30, 2021, the same day the claimed vulnerability was disclosed, and last updated on July 2:
Looking at the changelog for Cooked as of WPScan’s last update, you can see that there isn’t an entry for version 1.7.5.6:
1.7.9
** NEW: Added an
inline_browseoption to the[cooked-browse]and[cooked-search]shortcodes. Ex.[cooked-browse inline_browse="true"]This will show the taxonomies inline and not require the “Browse” button being clicked to view them.1.7.8.5
- FIX: Fixed an issue with large spaces between the recipe template shortcodes
- FIX: Fixed an issue with Vimeo videos in the gallery
1.7.8.4
- FIX: Removed “Section Headings” from recipe schema output.
1.7.8.3
- FIX: Another patch release for taxonomy title bugs (sorry!).
- FIX: This particular patch prevents the navigation items from getting renamed.
1.7.8.2
- FIX: Another patch release for taxonomy titles.
1.7.8.1
- FIX: Patch release for some quick taxonomy title fixes.
1.7.8
- FIX: Page titles are now updated on taxonomy pages (categories) when Browse Recipes page is used.
- FIX: An additional quick PHP 7.4 fix.
1.7.7
- FIX: Support for PHP 7.4 and WordPress 5.5.
1.7.6
- NEW: An optional recipe field has been added for “SEO Description”. In the Recipe Schema output, this field will take precedence over the “Excerpt” field.
- NEW: Added a new “Advanced” option to disable the recipe schema output that Cooked generates.
- FIX: Fixed the 404 errors on Fotorama PNGs.
- FIX: Fixed the issues with videos not playing in the Cooked Gallery.
- FIX: If Servings are set to “1”, you can now Half and Quarter them in the Servings Switcher.
- TWEAK: Widgets with images now load thumbnail sizes instead of the larger ones.
1.7.5.2
- TWEAK: Adds support for Cooked Pro 1.7.
The same is true if look at how it was as of March 30, 2021.
Checking the development log confirms that not only does that version not exist, but that plugin had already moved past that as possibly being a version back in October 2019, as version 1.7.6 was released then.
The original report states the claimed vulnerability in Cooked pro was fixed on March 30. There wasn’t a version of Cooked released then or for several months.
What looks to have happened here is that WPScan did absolutely no due diligence before claiming that the vulnerability existed in Cooked and was fixed, considering they didn’t even look to see if the version they claimed it was fixed in existed. Despite that, they claim they verified this:
This is far from the first that WPScan has run with inaccurate information. One previous example we noted in June, involved an instance where they claimed a vulnerability had been fixed, which hadn’t been fixed. We are not the only ones to have recently noted that they are not providing accurate information about vulnerabilities being fixed. Automattic, through their Jetpack blog, did the same thing in August, though obliquely, and while not noting that they rely on WPScan’s data, despite knowing it isn’t accurate.
Why is Automattic Sponsoring This?
Speaking of Automattic, they not only use WPScan’s unreliable data, but WPScan claims they sponsor them:
Why would a major player in the WordPress, especially one in the WordPress security space (Jetpack is marketed first as a security plugin), sponsor a company that clearly isn’t concerned whether what they are claiming is true or not? Including doing that with Automattic’s own plugins. We are going to contact Automattic and ask them. We will update this post if they do, though they probably won’t respond, considering they already are aware of the issue and haven’t stopped funding the company.