WordPress Continues to Distribute Plugins They Know Contain Serious Unfixed Vulnerabilities
A week ago we had what look to be a hacker probing for the WordPress plugin Press Elements on one of our websites through a request for the following file.
/wp-content/plugins/press-elements/package.json
That plugin was removed from the WordPress’ plugin directory on April 5, 2021 for an unspecified security issue:
We couldn’t find any information about a vulnerability being disclosed after that or around that time that could explain that closure.
Looking at our data set, we found the plugin had had a serious publicly disclosed unfixed vulnerability for over two years before that. The vulnerability would allow anyone logged in WordPress to change arbitrary WordPress settings (options) and through that they create new WordPress accounts with the Administrator role. The vulnerability was caused by the inclusion of the Freemius library, which a hacker had discovered contained the vulnerability and started exploiting it.
The vulnerability was resolved in February 2019 and we had warned about it at the time, but somehow the team running the WordPress Plugin Directory left this plugin known to be using a vulnerable version of the library in the plugin directory for over two years. We used to make sure that type of situation didn’t occur, but we suspended doing that because of continued poor handling of security on WordPress’ part. Based on that situation, other WordPress security companies clearly haven’t been interested in making sure that situation isn’t occurring, despite claims about the concern for the security of WordPress websites.
Despite being known to be vulnerable, as of March 2021, the plugin had 20,000+ active installs. That is the same install count it had as of April 2019.
WordPress hides the install counts of plugins once they have been removed, so it isn’t clear how many websites are still using the plugin, which would be important to understand if websites are still using plugins after being removed from the plugin directory for security issues. Considering that WordPress has refused to warn inside of WordPress that insecure plugins are being used, it seems possible that remains rather high.
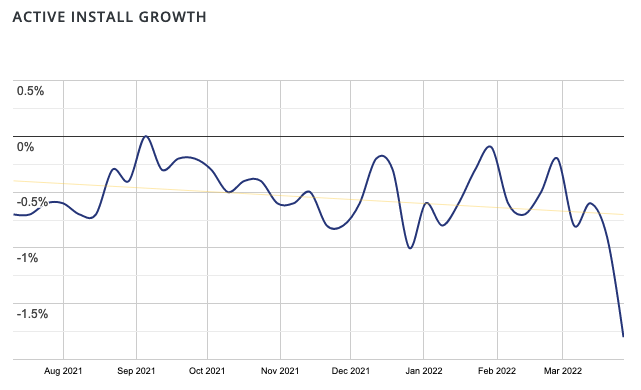
While the install count is removed for close plugins, WordPress leaves up other statistical information. One of those is active install growth, which suggests that not a lot of websites have been removing the plugin from July 2021 to the present:
Another of the stats still available seems odd, as they continue to chart the number of downloads of the plugin per day. It seems like that should be 0 per day, since the plugin was removed, but that isn’t the case:
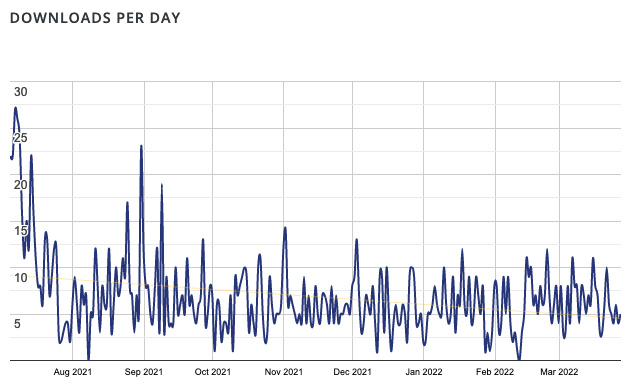
Checking further on this, we found that WordPress removes the download link for removed plugins, but continues to distribute the plugin, if you request the download URL for it. That seems like a bad idea.
Easy Improvements Possible
While this highlights how things are going wrong, it also highlights easy changes that could be made to improve the situation. It would be easy to make sure that known vulnerable plugins don’t remain in the plugin directory. It also should be easy to stop providing a download of plugins that have been removed from the plugin directory. It also would be relatively easy in situation like this to provide a fixed version, since the vulnerable library was fixed. It also wouldn’t be too hard to warn people that they are using a plugin known to be vulnerable.
Other than the download issue, those improvements are things that we and others have been bringing for years. Yet, WordPress has steadfastly refused to fix them, for reasons that don’t make sense (including that one of the principal people with control over these things believes that “magic wizards” discover exploitable vulnerabilities).