A Month Later, WordPress Still Hasn’t Taken Action for Websites With Backdoored Plugin They Distributed
On Februrary 28, we publicly warned that the WordPress plugin Mistape had what appeared to have a backdoor added in its latest release. Part of the code would contact the developer’s website and let them know if the plugin was installed. Another part would allow anyone to gain access to an account on the website with the Administrator role. The response from WordPress was to close the plugin in their plugin directory:
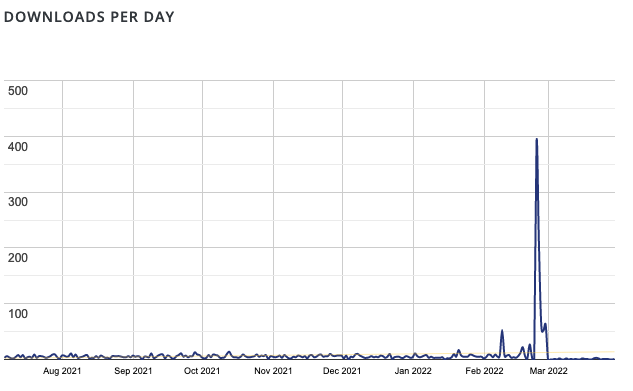
That prevented anyone more from updating the plugin through WordPress, but it did nothing for those that already got the new version since it was released on February 24. Based on the download chart provided by WordPress, hundreds had already updated (the download chart includes anyone updating the plugin through WordPress):
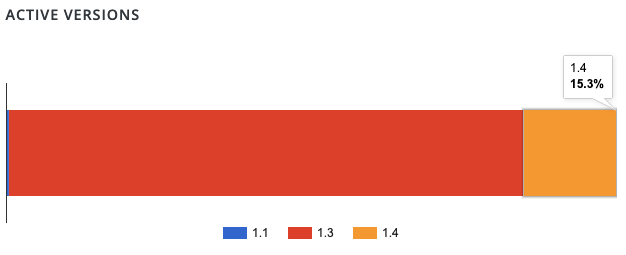
We don’t know how many installs the plugin has now, but before it was closed it was somewhere between 3,000 and 4,000 according to WordPress. According their data, 15.3% of those using the plugin are running version 1.4, which is the affected version:
For reasons that don’t make sense, the team running the Plugin Directory refuses to warn people they are using known vulnerable plugins, so there is not a warning being provided by WordPress to websites using the plugin.
While they rarely use it, that team has the ability to release a new version to address a vulnerability and that could have easily been done here, by simply releasing the previous version as an update. That hasn’t happened. (They can provide an update to existing users of the plugin without making it available to those not already using it, which rules out that being an issue with that approach.)
It would be easy to have better handled this situation, but unfortunately, WordPress is able to get away with not properly handling situations like this.
Still Being Downloaded
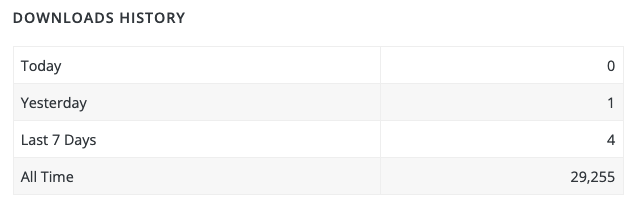
As we noted earlier this week with another plugin, it turns out that WordPress continues to distribute plugins even after they are closed, and there are still some people downloading the backdoored version:
WPScan and Patchstack Not Warning About This
What makes that lack of warning from WordPress more troubling is that the head of WordPress, Matt Mullenweg, runs a company, Automattic, that has a service that sells access to just that type of information. That service, WPScan, is marketed with the claim that they are the first to warn about such a situation:
Be the first to know about vulnerabilities affecting your WordPress installation, plugins, and themes.
Considering we are a competitor of theirs, they wouldn’t be the first to warn in a situation like this, but in reality a month later they are still not warning about this:
(They intentionally don’t warn about vulnerabilities we discover, again, for a reason that doesn’t make sense.)
Another of our competitors, Patchstack, makes the same claim about being first:
Be the first to know about new vulnerabilities!
Like WPScan, they have failed to warn about this.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade
F… I did not see your previous post about Mistape and it’s a plugin I love. I understand know why I received some strange reports what had no sense. How to know if the site has been compromised ? I have Ninja Firewall installed and it did not detect any admin login or new file.
We are sorry that WordPress didn’t provide a warning to you once they knew about this.
If you are using version 1.4, then it would probably be a good idea to assume that you have been compromised and go from there.
Since the login doesn’t involve the normal login process, it might not get logged, depending on how a plugin handles that. We haven’t looked into that element, but it seems like something worth checking on.