The Wordfence Security Plugin Isn’t Actually Protecting Against Brute Force Attacks
We recently had a potential customer ask if our firewall plugin protected against brute force attacks as they believed the Wordfence Security plugin is doing. They also noted that using something different than what Wordfence Security provides would seem like less protection, even if it was better protection. When it comes to brute force attacks, they have hit the nail on the head, as those are not even happening. Wordfence is pretending something that WordPress already provides effective protection against isn’t happening and instead brute force attacks are happening, which requires something that WordPress doesn’t have built-in protection against.
Here is how Wordfence describes brute force attacks:
Fundamentally, a brute force attack is exactly what it sounds like: a means of breaking in to the back end of a website with relentless successive attempts.
Those are not happening. You don’t have to look any further than Wordfence’s own data. Here are the numbers of attacks attempts they have claimed to have blocked recently across the website’s using their plugin:
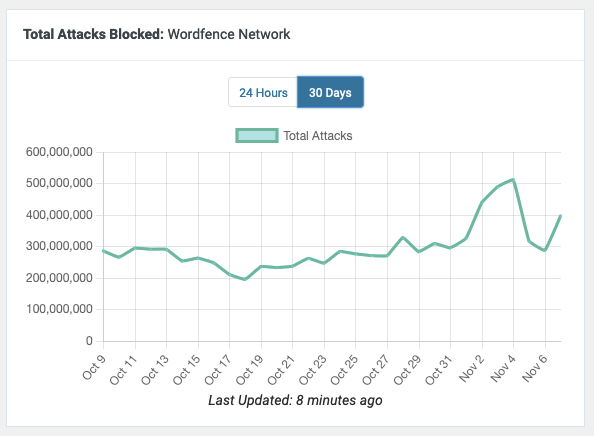
The high point of that was 509 million attacks in a day. That sounds like a lot at first, but that was across between 4 and 5 million websites. So at most that was 127 attempts per website. That isn’t anywhere attempts enough for brute force attacks.
Let’s say you had a very simple password, which was only made up of four digits from 0-9. There are 10,000 possible combinations. With a expanded range of characters and number of characters, the number of possible combinations grows exponentially.
Let’s say you instead had a six character password with a combination of lowercase letters a-z and digits from 0-9. Then there would be 1,838,265,625 possible combinations. If you assume that on average an attacker would guess the password after they have tried half the possible passwords, then there would be more combinations they would have to try then Wordfence Security stopped across at least 4 million website in one day!
So something else must be going on. But what?
We recently logged failed login attempts on our website to see again what is really going on. One larger recent example of an attack involved 220 login attempts from one IP address. Here are the passwords that were tried:
- !
- pluginvulnerabilities
- 00
- 000
- 0000
- 000000
- 1
- 102030
- 111
- 1111
- 111111
- 11111111
- 112233
- 11223344
- 121212
- 123
- 123123
- 123123123
- 123321
- 1234
- 12341234
- 12345
- 123456
- 1234567
- 12345678
- 123456789
- 1234567890
- 123456a
- 1234abcd
- 1234qwer
- 123654
- 123qwe
- 123qweasdzxc
- 147258
- 147258369
- 159753
- 1q2w3e4r
- 1q2w3e4r5t
- 1qaz2wsx
- 55555
- 654321
- 666666
- 987654321
- a
- a12345
- a123456
- a1b2c3d4
- aaaaaa
- abc123
- abc12345
- abcd1234
- admin
- admin1
- admin123
- admin123456
- admin2017
- admin2018
- admin2019
- admin2020
- adminadmin
- administrador
- administrator
- adminpass
- amazon
- apple
- apple123
- asd123
- asdf1234
- asdfgh
- azerty
- changeme
- demo
- hello
- letmein
- nopass
- pa55w0rd
- pass
- pass1
- pass123
- password
- password1
- password123
- q1w2e3
- q1w2e3r4
- q1w2e3r4t5
- qazwsx
- qazxsw
- qwe123
- qwer1234
- qwerty
- qwerty123
- qwertyuiop
- root
- secret
- success1
- temppass
- test
- test1
- test123
- test1234
- testing
- testtest
- webmaster
- welcome
- welcome1
- zaq123
- zaq12wsx
- zxcvbnm
- zzz
- coronavirus
- !
- pluginvulnerabilities
- 00
- 000
- 0000
- 000000
- 1
- 102030
- 111
- 1111
- 111111
- 11111111
- 112233
- 11223344
- 121212
- 123
- 123123
- 123123123
- 123321
- 1234
- 12341234
- 12345
- 123456
- 1234567
- 12345678
- 123456789
- 1234567890
- 123456a
- 1234abcd
- 1234qwer
- 123654
- 123qwe
- 123qweasdzxc
- 147258
- 147258369
- 159753
- 1q2w3e4r
- 1q2w3e4r5t
- 1qaz2wsx
- 55555
- 654321
- 666666
- 987654321
- a
- a12345
- a123456
- a1b2c3d4
- aaaaaa
- abc123
- abc12345
- abcd1234
- admin
- admin1
- admin123
- admin123456
- admin2017
- admin2018
- admin2019
- admin2020
- adminadmin
- administrador
- administrator
- adminpass
- amazon
- apple
- apple123
- asd123
- asdf1234
- asdfgh
- azerty
- changeme
- demo
- hello
- letmein
- nopass
- pa55w0rd
- pass
- pass1
- pass123
- password
- password1
- password123
- q1w2e3
- q1w2e3r4
- q1w2e3r4t5
- qazwsx
- qazxsw
- qwe123
- qwer1234
- qwerty
- qwerty123
- qwertyuiop
- root
- secret
- success1
- temppass
- test
- test1
- test123
- test1234
- testing
- testtest
- webmaster
- welcome
- welcome1
- zaq123
- zaq12wsx
- zxcvbnm
- zzz
- coronavirus
What you are seeing there are the results of a dictionary attack. In that type of attack, the attacker tries to login using common passwords. As suggested by Wordfence’s own data, the attacks are not relentless, but very limited. Before we further discuss the implications of that, there is a another important element of that attack to note.
Here are the corresponding usernames used for those login attempts:
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- pluginvulnerabilities
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
- admin
Neither of those usernames exists on our website. So the attack would have failed no matter what password was used. If an attack failed on its own, then Wordfence hasn’t really provided any protection.
Why This Matters?
One issue with what Wordfence is doing there is making it seem that solutions focused on real threats are failing to provide protection they are offering. That is a big problem when their plugin fails to provide the protection against real threats that other options do. That is made worse when their plugin causes a significant performance hit, which competing plugins that provide more protection don’t impose.
Another issue is that Wordfence is trying to scare people by making it seem like hackers are relentlessly attacking their websites when they are not.
Yet another issue with this is that this kind of protection is that it can lead to legitimate users being blocked from logging in to the website without stopping any attacks that would have succeeded. (Blocking legitimate requests is a wider problem with their plugin.)
The biggest problem with all this is that Wordfence’s solution doesn’t actually address the real problem here. If someone were really using a weak password that could be guessed by a dictionary attack, then Wordfence’s solution is easily bypassed. All a hacker has to do is to limit the number of consecutive attempts it makes from an IP address and the protection never comes in to play.
By comparison, WordPress’ built-in solution for this, a password strength meter will always work as long as it is used. If someone has user they can’t trust to use a strong password, they probably shouldn’t have much access to the website, but the solution their would be to use a plugin that simply requires strong passwords.
So Wordfence is pretending a non-existent threat is happening, while hiding a real threat that their plugin isn’t the right solution for.