Wordfence Is Warning That Vulnerabilities Are Critical When They Are Not
Whether intentionally or not, part of the business model of the developer of the Wordfence Security plugin involves scaring people in to buying their services by overstating the risk posed by security issues. The overstated risk was on display in the last week with a false claim of “critical” vulnerability in the current version of WooCommerce.
As we noted yesterday, Wordfence had claimed that there was a vulnerability in a version of WooCommerce, which they later admitted didn’t contain the vulnerability. This was caused in part by them not actually checking on a patch they claim had been released in a certain version. There wasn’t a patch. Even after admitting that mistake, they still didn’t check to see if there really was a vulnerability. Instead, they, for some reason, thought that WooCommerce’s developer claiming that they had addressed the “potential for” a vulnerability, meant there was a vulnerability. There wasn’t a vulnerability. Only the potential for one, as WooCommerce’s developer had clearly stated.
If you check into this now, you can see that they are claiming the vulnerability is of “medium” severity, but also claiming it is a “critical” issue:
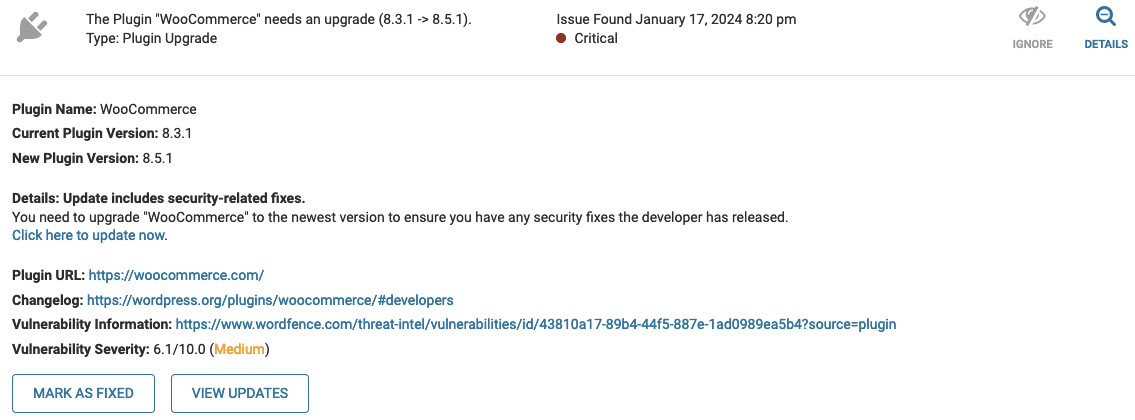
Those two things seem at odds.
The claimed type of vulnerability, reflected cross-site scripting (XSS), is not a big concern and not a critical issue. Something a Wordfence employee sort of admitted to, while falsely claiming the vulnerability existed:
While Cross-Site Scripting vulnerabilities can have Critical impacts, the threat posed by this particular vulnerability is fairly low – don’t click on any suspicious links, and make sure you have a firewall like the Wordfence Firewall installed, and you’ll be fine.