Wordfence Intelligence Vulnerability Data Feed Keeps Looking Worse
Yesterday, we detailed significant discrepancies between the way the WordPress security provider Wordfence marketed their Wordfence Intelligence service and the actual results they are delivering with that. Much of that affects those also relying on their Wordfence Security plugin as well. One aspect that affects users of their plugin, as well as other plugin developers, is Wordfence’s information on vulnerabilities in WordPress plugins. As of yesterday, they marketed that part of Wordfence Intelligence this way:
Vulnerability Detection at Scale
Wordfence Intelligence includes a comprehensive and extremely current vulnerability database for WordPress that contains nearly 7,000 unique vulnerability records. This database is actively maintained by some of the top WordPress vulnerability researchers in the industry. For hosting providers that are hosting WordPress websites for their customers, this product includes enough data to perform massively parallelizable scans on your server fleet for WordPress vulnerabilities, alert customers or your SOC with information that specifically identifies that vulnerability, and includes the data needed to mitigate the issue.
As of today, that had been significantly changed:
Wordfence Intelligence Vulnerability Data Feed
Includes over 7,000 WordPress-related software vulnerabilities and is continuously updated in real-time as new vulnerabilities in WordPress software such as plugins and themes are discovered and disclosed.
Removed were claims that it is a “comprehensive and extremely current vulnerability database” and that it is “actively maintained by some of the top WordPress vulnerability researchers in the industry”.
In our post yesterday, we mentioned our previous coverage of Wordfence falsely claiming the latest version of a WordPress plugin with 300,000+ installs contained a vulnerability. We ran across that through our monitoring the WordPress Support Forum for topics related to plugin vulnerabilities. More instances of the issue keep popping up.
More False Claims
One plugin developer wrote yesterday:
In another topic related to Wordfence claiming that the plugin contained a vulnerability, the developer’s message suggests that Wordfence had not contacted them about whatever was supposed to be the issue:
Thank you for informing about this. I have contacted the Wordfence guys to get more details on how to resolve this issue. I will be uploading an updated version asap, to satisfy their security scanner.
With a topic involving another plugin, the developer also didn’t appear to have been contacted by Wordfence about whatever they were claiming was an issue. A screenshot from the developer also showed that no details were being given about the claimed issue when warned about in Wordfence Security:
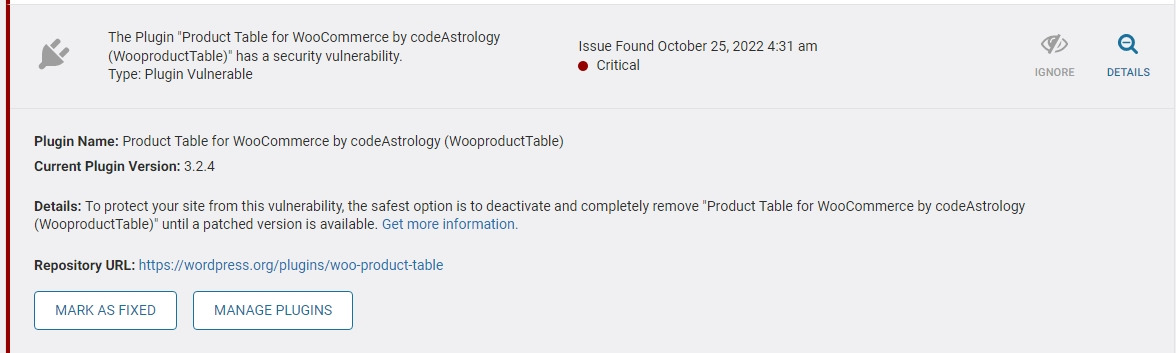
A Wordfence employee responded, saying that it was an error on their part that led to the warning:
We do apologize very much as that is an error on our part and we have removed your plugin from our vulnerability database.
But no explanation was given as to why there was an error.
There were multiple vulnerabilities found and fixed in that plugin earlier this year, so perhaps Wordfence didn’t correctly mark them as fixed.
Today, there was also someone claiming that they were being warned by Wordfence Security about a vulnerability in a plugin, despite using a version of the plugin newer than the vulnerability was said to be fixed in.
Wordfence Isn’t Alone in Low-Quality Data
Low quality data on vulnerabilities is not unique to Wordfence, they previously, without disclosing it, had relied on a source, Automattic’s WPScan, which has long had quality control issues. Another newer provider named Patchstack has also had major issues going back to its precursor ThreatPress, which was just a copy of WPScan’s data while claiming to be something else. But Wordfence’s data seems to be getting things wrong in a worse way than those other two.
What makes things more problematic for those trying to sort out what is really going on with the claims being made by the companies is they are often not providing enough information for their claims to be independently verified. WPScan often only provides a proof of concept and delays providing that for a while. That is better than Patchstack, which provides almost no details of what is supposed to be at issue. Wordfence is the worst, providing not even vague information on what the vulnerability is supposed to be, only saying that there is a vulnerability.