Wordfence’s Idea of Responsible Disclosure Involves Leaving Very Vulnerable Plugins in WordPress Plugin Directory
A week ago, we wrote about how a WordPress plugin being targeted by a hacker had remained in the WordPress Plugin Directory despite having an unfixed vulnerability that hackers would target. We had noted that the WordPress security provider Wordfence had known about the vulnerability, but hadn’t made sure the plugin was removed. While checking into a claimed vulnerability to add it to our data set, we found another instance of that, which is more troubling.
In February, a Wordfence employee named Chloe Chamberland wrote a strange post on Wordfence’s blog that claimed in the headline, “the WordPress ecosystem is becoming more secure with responsible disclosure becoming More Common”. It is strange because the body of the post never mentions the phrase responsible disclosure or makes any mention of it. Instead, the author seems to be trying to suggest that doing something other than responsible disclosure is responsible disclosure. Responsible disclosure involves notifying a developer of a vulnerability and giving them a chance to resolve it, before notifying anyone else. The post is actually suggesting directing reporting of vulnerabilities in WordPress plugins away from the developers and WordPress:
In addition to changes in code, one major factor in the increase of vulnerability reports in 2022 was likely the fact that it is becoming easier for researchers to report vulnerabilities. As was mentioned in our 2022 report, Wordfence, along with other companies, became a CVE Numbering Authority (CNA) in 2021. This means that there are more points of contact for researchers to submit newly discovered vulnerabilities, and more bandwidth for processing vulnerability reports. As mentioned in our report, we hope to continue to amplify this trend with the launch of Wordfence Intelligence Community Edition, a complete free to access and utilize WordPress Vulnerability Database.
That isn’t responsible disclosure. It is worse with Wordfence, since with their involvement with CVE’s CVE Numbering Authority (CNA) they are selling information on exploiting unfixed vulnerabilities they become aware through that to any hackers willing to pay.
Back when Wordfence became a CNA, the same employee wrote a post where they said this:
To report a vulnerability, even if there is uncertainty about the responsible disclosure process, proof of concept production, or mitigation review procedures, the Wordfence Threat Intelligence team is available to assist. Our highly credentialed team has expertise and experience in proper security disclosure and can assist in ensuring that adequate remediation of vulnerabilities, no matter the severity, are applied and verified.
Again, that isn’t responsible disclosure, since they are suggesting to not report vulnerabilities to the developers, but to them instead. But things get worse from there.
On March 11, an exploitable unfixed vulnerability in what was described as “a popular WordPress plugin” was disclosed. In reality, the plugin isn’t popular, unless you think a plugin with 80+ installs is popular. The vulnerability was publicly issued a CVE ID, CVE-2023-1372, on March 13 by Wordfence. The vulnerability hasn’t been fixed, so the plugin shouldn’t still be available in the WordPress Plugin Directory, and yet it is as or the publishing of this post it is:
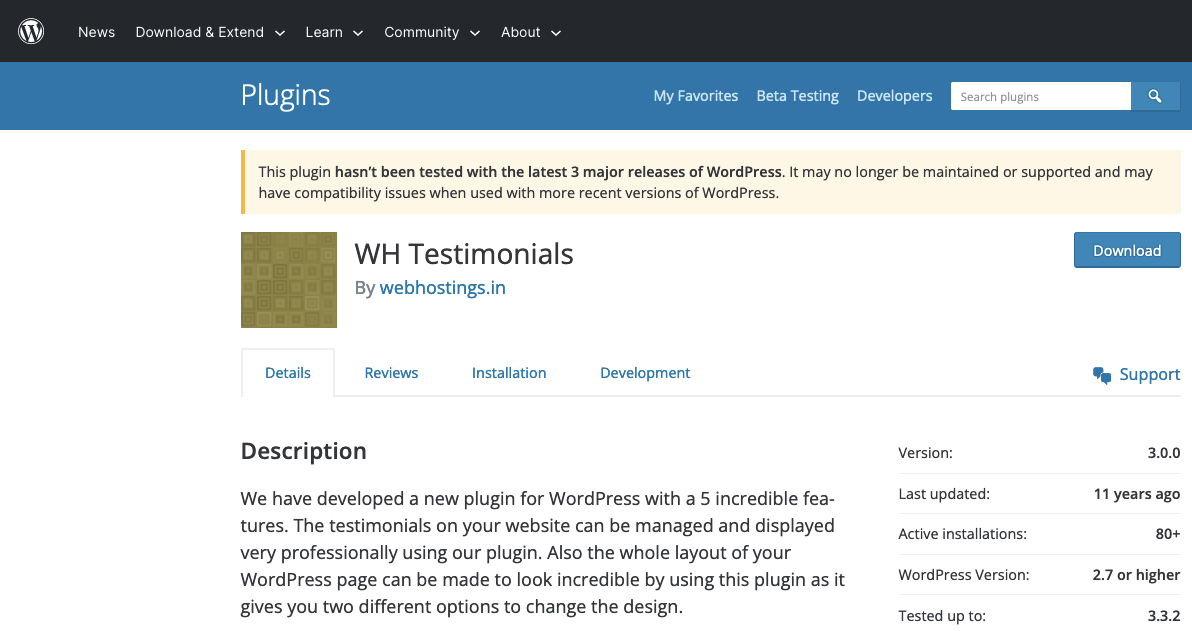
The discoverer of the vulnerability makes no mention of contacting the developer of the plugin or WordPress. They did contact Wordfence, who didn’t make sure this was properly addressed, contrary to the quote above about the expertise of their “highly credentialed team”.
WPScan and Patchstack Too
As with the situation last week, Automattic’s WPScan and Patchstack also know about the vulnerability, but haven’t made sure the plugin was removed from the WordPress Plugin Directory.
We used to make sure that known vulnerable plugins were removed from that, but we suspended doing that years ago because of continued bad behavior on WordPress’s part.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade