Wordfence Doesn’t Admit That WordPress Had Already Provided Protection for “Massive Exploit Campaign” Before Them
Where WordPress firewall plugins are really useful is for providing protection before a vulnerability is known about, as at that point they can offer protection that other solutions can’t. That was on display with a recent widely exploited zero-day that web application firewalls (WAFs) didn’t protect against, but two firewall plugins did.
Notably, though, the most popular WordPress firewall plugin Wordfence Security didn’t provide protection in that situation. That is a reoccurring situation. That isn’t surprising considering that the business model associated with the plugin is based on selling firewall rules for vulnerabilities once they are already known about (and more troublingly selling hack cleanups despite claiming their firewall “stops you from getting hacked”). If they provided the type of protection the two best firewall plugins do, it would largely remove the need for those rules. Incredibly, they refer to their belated rule based protection in their Wordfence Premium service as being “real-time” protection.
That creates a fairly obvious problem, since they are selling protection that would usually come in to play only after there is a better option, simply updating plugins. If providing an update isn’t enough, WordPress has a further solution to have serious security updates applied automatically. Wordfence’s response to that is to pretend that isn’t happening.
As we noted back in March, just such an automatic update occurred for a vulnerability that had been in the WooCommerce Payments plugin. We were not the only ones to note that at the time. Despite that, Wordfence has now brought up the vulnerability twice on their blog without noting that. The second time is more glaring.
A Wordfence post early this week was titled “Massive Targeted Exploit Campaign Against WooCommerce Payments Underway“. Here are the first three paragraphs of their post:
The Wordfence Threat Intelligence team has been monitoring an ongoing exploit campaign targeting a recently disclosed vulnerability in WooCommerce Payments, a plugin installed on over 600,000 sites. Large-scale attacks against the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks against 157,000 sites on Saturday, July 16, 2023.
The exploit allows unauthenticated attackers to obtain administrative privileges on vulnerable websites, rating it a Critical CVSS score of 9.8. This makes it an appealing target, and this attack campaign confirms our original coverage of the vulnerability that predicted large-scale attacks.
All Wordfence users, including Wordfence free users, have been protected against this vulnerability since April 22, 2023 via a Firewall rule we developed to block exploit attempts. Wordfence Premium, Care, and Response sites received protection even earlier, on March 23, 2023. Versions 4.8.0 – 5.6.1 of the WooCommerce Payments plugin are vulnerable.
Notice how they don’t even state in those paragraphs that the vulnerability has been fixed. In fact, nowhere in the post do they ever acknowledge it.
Before they even mention the vulnerable versions, they mention when they provided firewall rules. What they don’t mention is they only provided protection after the update was available and was applied automatically.
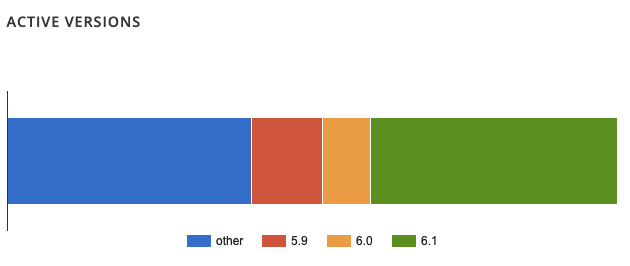
Something else that is obviously misleading is that they mention the install count of the plugin right out of the gate, but don’t mention that most of the 600,000+ installs couldn’t be vulnerable. (There were only 500,000+ installs when the vulnerability was fixed.) Here is the version breakdown shown on the WordPress Plugin Directory’s page with statistics for the plugin, which shows that the majority of installs are running at least version 5.9 of the plugin:
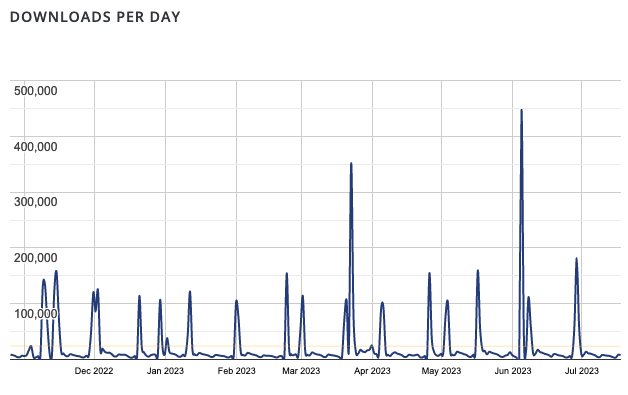
Right below that is a chart of downloads per day. That includes anyone updating the plugin. There you can see that the number of websites still running a vulnerable version couldn’t be all that significant:
No where in their post do they admit that WordPress protected websites from being hacked. What they do, instead, is make it sound like websites have been hacked, when they seem to be describing things that didn’t happen on websites that were actually hacked. We say that because they describe information that you wouldn’t have from a hacked website. Including information, that if it was really coming from a hacked website would suggest there is very serious security issues (including logging user passwords). Various journalists, including the Bleeping Computer’s Lawrence Abrams, fell for that misleading information.
Unsurprisingly, their conclusion fails to even to acknowledge that WordPress had taken action which prevented websites from being hacked or mention the importance of keeping plugins up to date:
In today’s article, we covered a number of tactics, techniques, and procedures used in a large-scale attack against sites running WooCommerce Payments. These attacks demonstrate significantly more sophistication than similar attacks we’ve seen in the past, including reconnaissance ahead of the main wave of attacks and multiple methods of maintaining persistence using functionality available to administrator-level users.
All Wordfence users, including Wordfence Free, Wordfence Premium, Wordfence Care, and Wordfence Response users are fully protected against these exploits. Additionally, the Wordfence scanner can help detect compromises even on sites that did not have Wordfence installed at the time of compromise.
If you know a friend or colleague who is using this plugin on their site, we highly recommend forwarding this advisory to them to help keep their sites protected. Please help make the WordPress community aware of this issue.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
Keeping plugins up to date would avoid websites getting hacked, which would take away from their business cleaning up hacked websites. Instead, they suggest forwarding their misleading post “to help keep their sites protected”.