WordPress Hides Accurate Information on the Security of WordPress Plugins, While Highlighting Inaccurate Information
Part of the mess we have seen when it comes to what can and can’t be mentioned about the security of WordPress plugins on the WordPress Support Forum is that accurate information about the security of plugins is often removed, while inaccurate information is often left up. That creates a situation where there is an incorrect belief that insecure plugins are secure and that insecure plugins are secure.
As example of that, a couple years back we had responded to a topic on the Support Forum where a couple of people were wondering if what looked like probing for usage of the plugin JQuery Html5 File Upload was related to a vulnerability being exploited. We had responded that the likely cause of that was a false report of a vulnerability of a type of that was likely to be exploited, which had been released the week before. The original poster had thanked us for that information and the marked the topic resolved. Three months later our reply and the one just thanking us were deleted, with no reason given, which seems very odd.
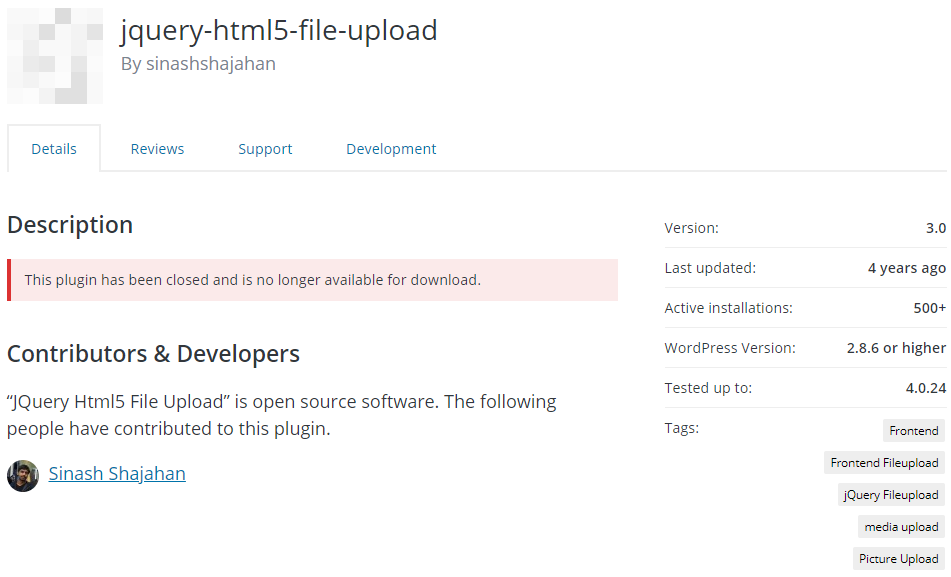
At some this point after that the plugin has been removed from the Plugin Directory for an unexplained reason:
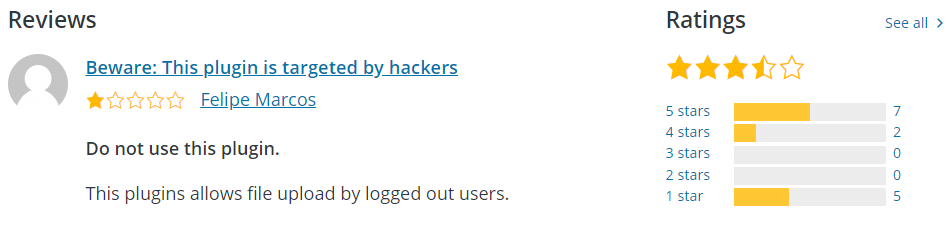
If you click over the to the reviews tab you see this review (reviews are part of the Support Forum):
It is true that the plugin allows for upload from logged out users, which isn’t any secret as the description of the plugin is:
This plugin adds a file upload functionality to the front-end screen. It allows multiple file upload asynchronously along with upload status bar.
The best you could argue is that maybe someone might place this on a password protected page and not be aware that wouldn’t limit usage to file upload capability.
The targeting by hackers would appear to be from the false belief that this could be used to upload .php files due to the false report of a vulnerability in the plugin, which wouldn’t be a good reason for a negative review. The upload functionality could be used by spammers to upload image files, but that is also true of a plugin developed by Automattic, WP Job Manager, which is available in the Plugin Directory despite that.
So the accurate information on what was going on was deleted while inaccurate information is left up. Making this type of thing worse is that the one of the reasons why the head of the Plugin Directory gave why websites using vulnerable plugins that have been removed from the directory can’t be warned about that is:
So that also is a huge part of the issue. There’s a lot more education than just slapping a rating on a vulnerability (which IMO is where most security sites miss the mark). I’m afraid, based on experience, that users will simultaneously think a situation is not as dire as all that and grossly over inflate the FUD factor :/
FUD being acronym for fear, uncertainty, and doubt, which is exactly what the actions of the people on the WordPress side of things are causing all the while refusing to provide people more information on the basis that providing could cause that. Unfortunately the people on the WordPress side of things have shown an inability to let others discuss on the forum that what they are doing is counterproductive, much less change their behavior to stop that from happening.