Plugin That Patchstack Is Claimed to Ensure Is Secure Contains an Additional Outdated Known Insecure Library
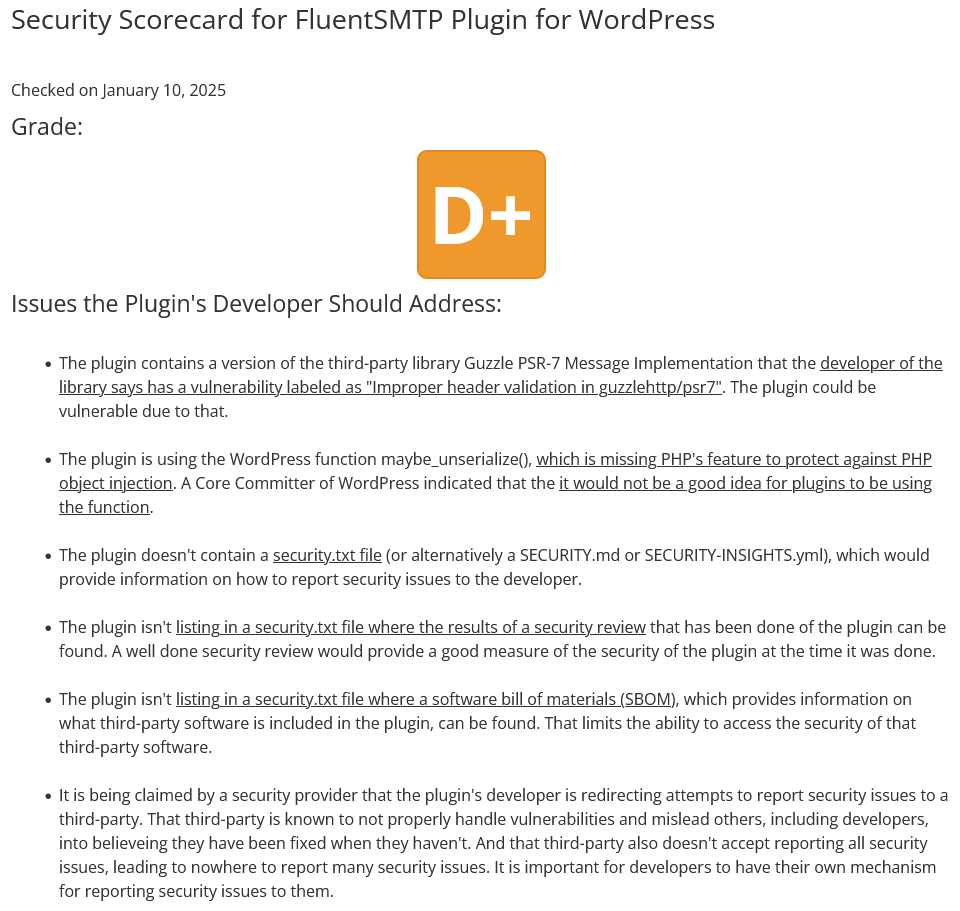
Last week we talked about two popular WordPress plugins that had been run through our Plugin Security Scorecard and identified as containing a rather out of date version of third-party libraries, which according to the libraries developers, contained a security issue. The libraries in question were different in the plugins, but it turns out they also have another library in common, where they are both using outdated known insecure versions. One of those is the 1+ million install SVG Support, where someone reported to the developer at the end of October that it was also using an outdated and known insecure version of the library DOMPurify. There still hasn’t been an update to the plugin to address that. More people have been reporting that issue. After seeing that, we started looking in to adding a check for DOMPurify to our Plugin Security Checker. Through that, we found a couple of fairly popular plugins are also still using older versions that the developer of the library is insecure.
We contacted the developer of one of those yesterday to let them know about the problem. The version they are using is subject to issues that were publicly disclosed by the developer of the library in September and October. There are not any topics on the support forum for the plugin about that, which is interesting considering the other plugin had multiple people reported it to the developer. [Read more]