Patchstack Apparently Didn’t Take Basic Step to Get Unfixed Exploitable Vulnerabilities Fixed Before Disclosing Them
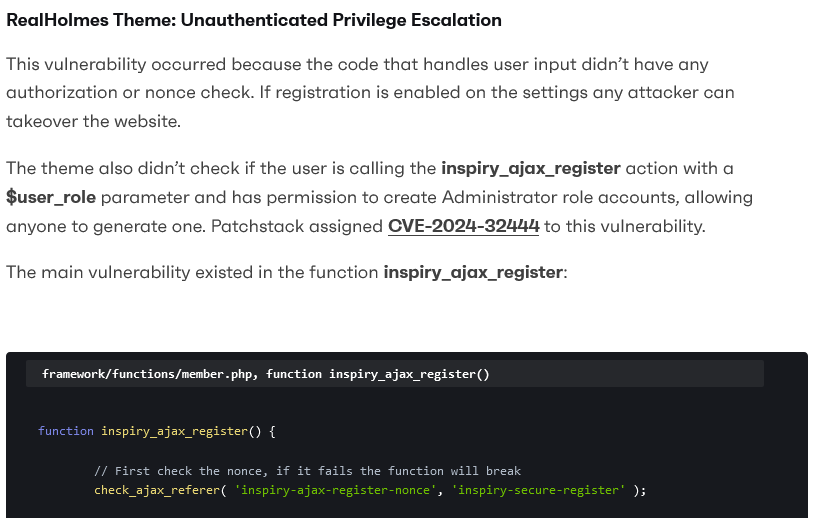
Last week WordPress security provider Patchstack disclosed what they claimed was an unfixed exploitable vulnerability in a WordPress theme and one in a related WordPress plugin. We say claim, because some of the information they provided appeared on its face to be very wrong. Early in the post, they wrote that “code that handles user input didn’t have any authorization or nonce check.” Code that handles user input doesn’t necessarily require authorization or a nonce check. For example, doing a search on a WordPress based website doesn’t require either of those things, despite involving user input. A more salient point is they then promptly showed the code and that not only contained a nonce check, but even had a comment about it, “First check the nonce, if it fails the function will break:”