WPScan and Patchstack Spread False WordPress Plugin Vulnerability Report That Looks Like Satire of False Report
One of the things we provide to customers of our service as part of our data set on WordPress plugin vulnerabilities is information on false reports of vulnerabilities. These days the source of many of those false reports is not who you would expect, as it is the two main other data providers. One of those, WPScan, claims that they are verifying these false reports and the other, PatchStack, is claiming to be providing patches for them. In both cases, what they claim to do flies in the face of them spreading obvious false reports. One of those reports is so bad it reads like it would be someone in the industry attempt at satirizing bad reports, not something being claimed to be real.
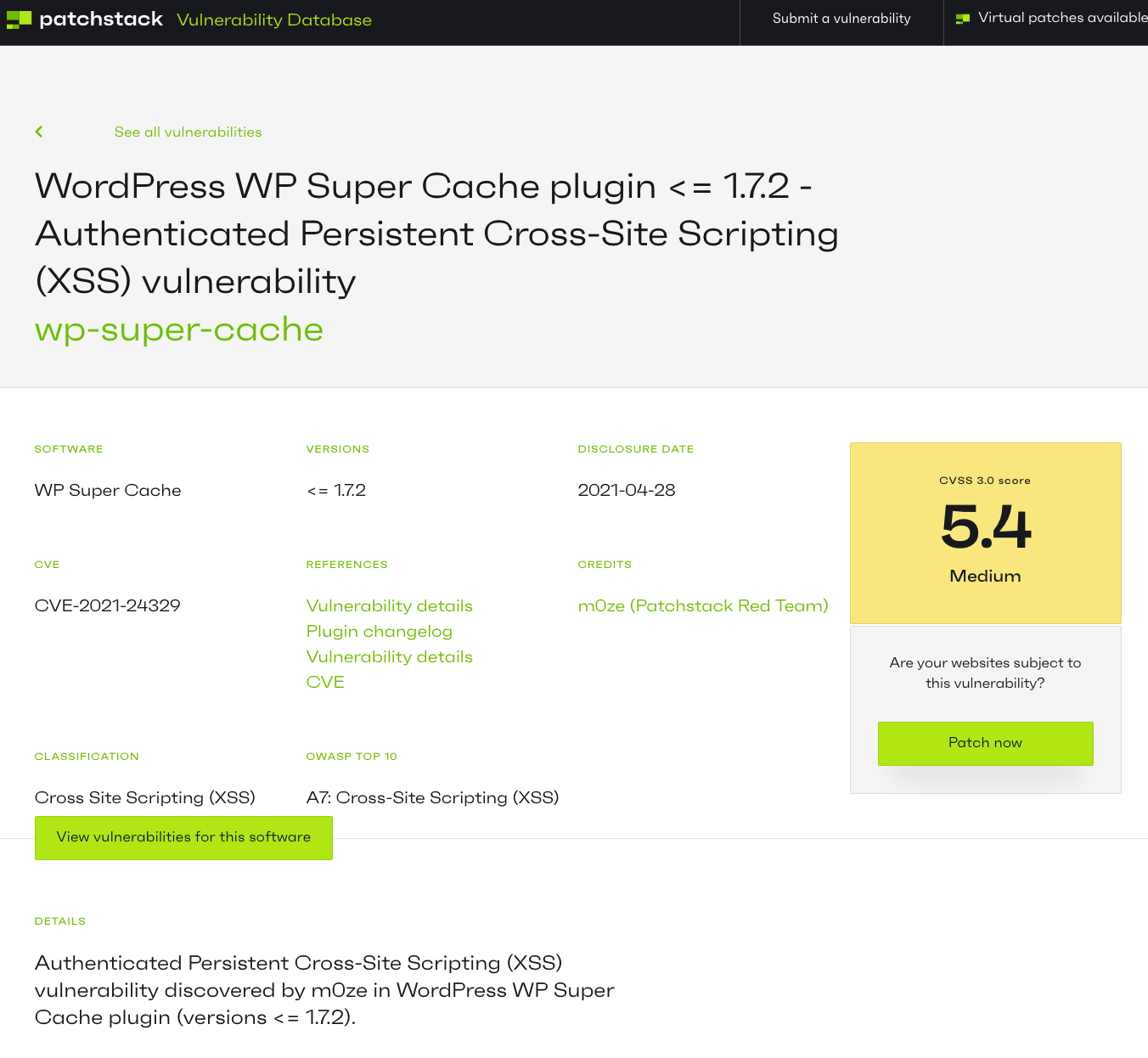
The report involves a plugin named Hotjar Connecticator, which was removed from the WordPress plugin directory at the time this report was released. The report was published directly with WPScan: [Read more]