It Would Be a Good Idea for WordPress Plugin Developers to Check Their Plugins with Our Plugin Security Checker
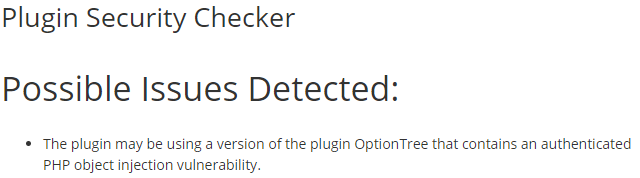
Yesterday we noted that the developer of the WordPress security plugin Security Ninja plugin isn’t doing a great job with the security of their plugins. In the latest example, they could have spotted an issue before we are publicly disclosing it by simply checking the plugin with our Plugin Security Checker, which identifies possible security issues in WordPress plugins. While looking into the details of another instance of them fixing a vulnerability we had identified in one of their plugins while working on an improvement to the Plugin Security Checker, this time with the plugin Nifty Coming Soon & Maintenance page we ran the plugin through our tool and saw that it got flagged for possibly including a vulnerable version of the plugin Option Tree: