Thousands of Websites Still Using WordPress Plugin that Has Vulnerability That Started Being Exploited Over a Year Ago
One of the ways that we keep track of vulnerabilities in WordPress plugins is by monitoring our websites and some third-party data for evidence of hackers are targeting plugins. Earlier this week that lead to us to us looking into a couple of plugins and finding vulnerabilities that hackers may be interested in, we have yet to get any definitive timetable on when or if those will be fixed by the developers, despite asking for that (the only response was that they would look into the issues), so we will probably be disclosing those tomorrow since hackers may already targeting something in the plugins. In the meantime, yesterday we had a request that looked to be probing for the plugin Form Lightbox:
/wp-content/plugins/form-lightbox/readme.txt
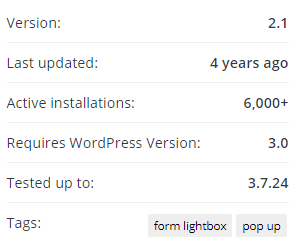
That plugin was removed from the Plugin Directory in July of last year after a hacker started exploiting a vulnerability in it. It used to be when that happened that the page on the Plugin Directory for the plugin would disappear. Recently things have changed so that the page remains and previously removed plugin’s pages have returned. One of the things that means is that you can see how many active installations a removed plugin still has. As of the time the plugin was removed it had 10,000+, which indicates that there were between 10,000 and 19,999 installations of the plugin.
As of today the plugin still 6,000+ active installations:
So there are still 6,000 and 7,000 websites still using it, despite having a vulnerability that hackers have exploited and still could as the vulnerability was never fixed. It’s possible that on some of those websites the vulnerabilities has been resolved by modifying the plugin, but we would guess that didn’t happen with many of them.
With that change it also easy to access the support forum for removed plugins and see what has been mentioned since they were remove. One the threads started since this plugin was removed shows the problem of not telling people why plugins have been removed, as people will still being looking to start using the plugin and not knowing that there is an issue.
It seems odd to us that WordPress would decide to display the number of active installs in this situation as it would make it easier for hackers to decide what vulnerabilities are worth targeting, while not warning people that it contains a vulnerability, which hackers appear to have been aware of before anyone else with this plugin.
Avoiding Using Vulnerable Plugins
There are a couple of obvious things that people on the WordPress side of things could do to help in situation like occurred with this plugin. The first would be for WordPress to notifying people using a plugin with a known vulnerability that it has a known vulnerability. Another one would be for WordPress to release a fixed version, something that they currently only do in rare occasions and when it came to this plugin they didn’t even want to have a discussion about doing (we would be happy to help with them with fixing those vulnerabilities). Better handling unfixed vulnerabilities isn’t being helped by the fact that WordPress founder Matt Mullenweg claims that the issue is “hypothetical”.
Another solution here is for people to be using our service’s companion plugin as the free data that comes with that warns about plugins that hackers are targeting, so anyone using our plugin and Form Lightbox would have been warned about the issue shortly after the exploitation started.
Our plugin is often the only free source of vulnerability information that warns about exploited vulnerabilities, despite it being possible for others to look at the data included in that and the information on our website. One recent example of that involves an arbitrary file upload vulnerability in the most recent version of the plugin PHP Event Calendar, which we disclosed and added to the plugin’s data on November 27. More than two weeks later none of the other free sources we are aware, which are the WPScan Vulnerability Database, ThreatPress Vulnerability Database, the plugin CWIS Antivirus Scanner, or the post of the website WPCampus, have included it.
If you are thinking that avoiding plugins that have been removed from the Plugin Directory would protect you from unfixed vulnerabilities, that used to be the case, but these days it isn’t because we were about the only ones making sure that vulnerable plugins were getting removed and since we suspended doing that due to WordPress continued poor handling of security, no one else has taken over doing that. That currently means that plugins with millions of active installations contain known vulnerabilities in the latest version. If you were using our service you would be warned if you were using those as well having us available to help you in taking action to protect yourself (we often can provide a workaround until the developer fixes the vulnerability or until you can move off of the plugin).