WordPress Plugin With Unfixed Vulnerability Targeted by Hacker Remains in Plugin Directory
For some time, we have been seeing a hacker probing for the usage of various WordPress plugins with known vulnerabilities across numerous websites. Many of those vulnerabilities have been SQL injection vulnerabilities. Over the weekend we saw them looking for usage of the WordPress plugin Gift Voucher. That isn’t surprising considering that there is an unfixed SQL injection vulnerability that was publicly disclosed by Tenable on March 22. What is surprising is that the plugin is still available in the WordPress Plugin Directory as of now:

We used to make sure that known vulnerable plugins were removed from that, but we suspended doing that years ago because of continued bad behavior on WordPress’s part. Other security providers know about the vulnerability but haven’t made sure it was removed.
That includes the Automattic’s WPScan:

That company is run by the head of WordPress, Matt Mullenweg. (He also directly employs half the team running the Plugin Directory.)
Wordfence also hasn’t made sure it was removed.

And Patchstack:
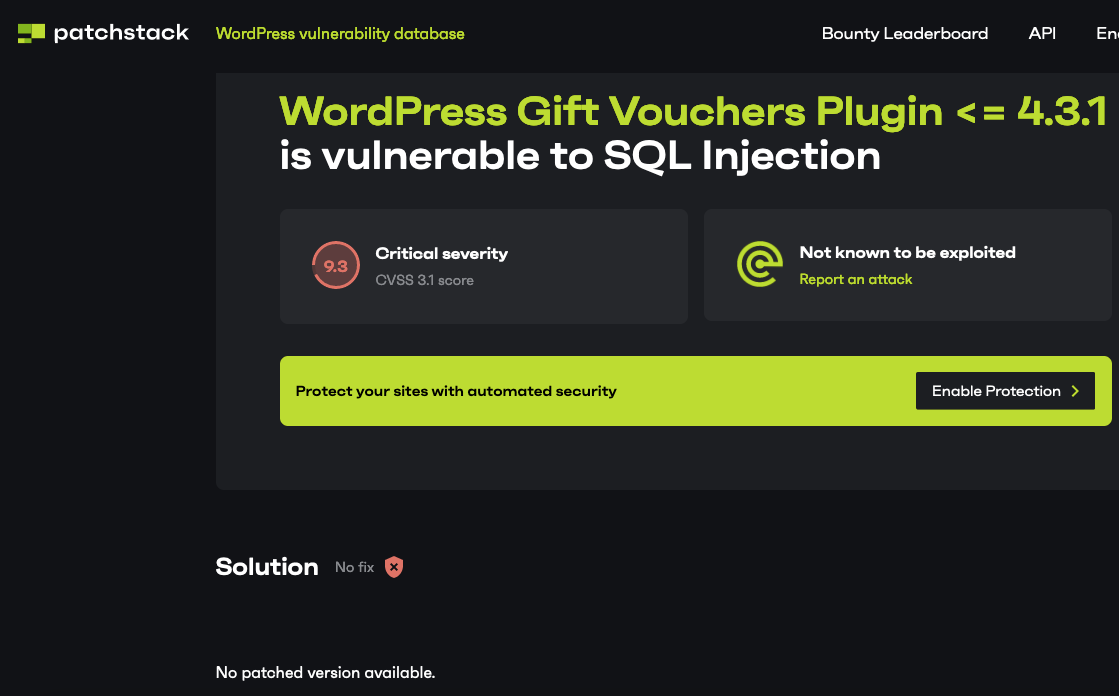
It isn’t as if WordPress isn’t aware of this. The WordPress’ support forum is micromanaged by problematic moderators who often get in the way of discussions about security issues, so it seems hard to believe they missed this, as there was a topic created about it on March 27.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade
Plugin vulnerabilities should be handled in private. It’s a security issue. Hey look, this is the security hole in a popular plugin, please don’t use it to hack other websites, give us 24-48 hours and we will fix things.
It’s appear the discloser contacted WordPress about this on December 19. But in any case, it was publicly disclosed on March 22, so the developer has had more than 48 hours to fix this and hasn’t. None of that is really relevant to the issue at hand, which is that the plugin has remained in the Plugin Directory despite being publicly known to be vulnerable.