WPCampus and Paul Gilzow Spreading False Information About Claimed Vulnerabilities in WordPress Plugins
One of the striking and telling aspects of the security community that seems to go a long way to explaining why security, whether of WordPress websites or more broadly, is in such bad shape is the lack of concern for providing accurate information. We often find that security companies are telling outright lies (or they are so unfamiliar with the basics of security that they have no idea that they are not telling the truth and shouldn’t be in the security industry). When it comes to security researchers, security professionals, or security journalists we have recently found over and over an apparent complete lack of concern that they might be providing information that isn’t accurate and lack of understanding why that others might take issue with that. That leads to a situation like if you tried to build the foundation of a home on quicksand, as can be seen by news coverage of security breach after security breach.
Along those lines we had recently tried to leave comments to point out that information on WordPress plugin vulnerabilities put out in posts on the website WPCampus and written by Paul Gilzow, who is described as a “Web application security and accessibility evangelist. Software instructor. Conference lecturer and presenter.”, is not accurate. While WPCampus’ code of conduct shown in the footer of their website states “All participants should be able to engage in productive dialogue. “, they don’t seem to be interested in a dialogue at all, as our comments haven’t been shown and the issues raised have not been resolved.
No Existent Files
To give an example let’s take a look at a few of the entries from their post from last week. On the same day as their post, we had written this about a claimed vulnerability in the plugin Ultimate Member:
They were at it again with a claimed cross site request forgery / shell upload vulnerability in Ultimate Member. In this case they claim that there is vulnerability in the latest version of the plugin involving files that don’t exist in it.
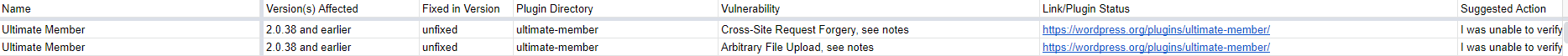
The information provided with WPCampus’ post includes that claimed vulnerability:
The first thing to note there is that for some reason the single cross-site request forgery (CSRF) vulnerability has been broken in two, which is a reoccurring issue with their reporting. A CSRF vulnerability involves causing someone to take an action they didn’t intend to, so the second part of the vulnerability refers to what action can be taken and therefore splitting them up doesn’t really make sense.
We don’t know how someone could think the vulnerability existed in that version of the plugin or is unfixed, seeing as we noted last week, the supposedly vulnerable files don’t exist in it. The “suggested action” given for that is, well, confusing:
I was unable to verify this vulnerability before posting. Researcher has history of misidentifying vulnerabilities. Remove, or see source for temporary fix
They say they are unable to verify it, but they suggest removing it. Considering that plugin has 100,000+ active installations according to wordpress.org and the plugin is likely rather central to many websites using it, that sort of recommendation seems quite problematic. We left a comment noting the report was false, but people visiting the post haven’t had the chance to be warned.
Not Really a Vulnerabilities Either
In the same post that we noted the problem with that report on Ultimate Member we also noted false reports of vulnerabilities disclosed last week in the plugins WP User Manager and Parallax Scroll, those are also incorrectly listed in the WPCampus’ information:
Unfixed
Even with an actual vulnerability they are providing information that is inaccurate and without a good reason for the mistake that we can think of. Last week we disclosed that the plugin Accessibility Suite by Online ADA contained a SQL injection vulnerability. According to their information it has been fixed in version 2.0.10:
That isn’t the case and we don’t what would lead someone to believe that. The changelog entry for that version doesn’t suggest that:
Bug fix: Fixed issue with wordpress installations in subdirectories not comparing properly in the sitemap and CSV download path
There was a change made to code related to the vulnerable functionality in that version, but nothing that should have impacted the vulnerability. It is easy enough to double check that, as we provided a proof of concept for the vulnerability and that continued to work with that version.
Wrong Versions
One final quick example of the problems with their information, though of less concern, unless you need accurate information on vulnerabilities in WordPress plugins. They include an entry for a vulnerability in Quiz And Survey Master, that was re-disclosed last week (we had previously disclosed it in September). While the information provided with their post claims it impacts “all” versions:
It actually only impacts version 4.5.5 and above.
A Change Should Happen
Just based on that anyone relying on those posts is getting a lot inaccurate information. Clearly something should be done about that and hiding comments noting there are problems isn’t a benefit to those reading those posts.
Part of the problem with what is going on here is that people believe that they can get the kind of data that we do a lot of work to provide, but for free, which as this post gives you idea of, you can’t actually. For people that need this kind of data and could afford our service and, the money not going to us means that we can’t do more to improve the security of WordPress plugins than we already do, which makes everyone using WordPress less secure.