Automattic’s Idea of Coopetition Involves Copying Data From Competitors Without Credit
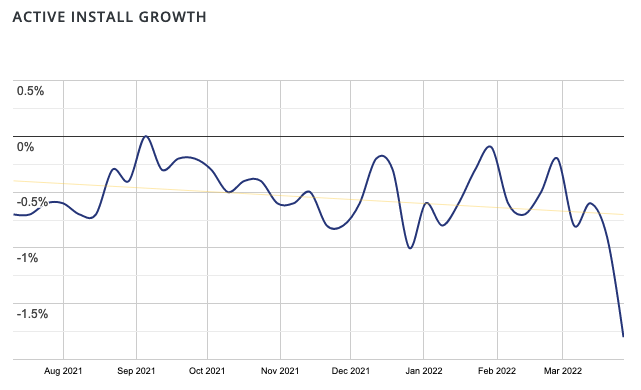
Companies operating in the WordPress space have to deal with a problematic situation. While WordPress is promoted as an open source community, the head of WordPress, Matt Mullenweg, uses his various entities to exert control and influence over the community to the benefit of his business interests. One of those entities is the news outlet the WP Tavern, which, when covering him, doesn’t disclose it is owned by him and its writers work for him. That lack of disclosure occurred again with a recent story about one of his employees causing WordPress to hide information useful to competing companies .
In the story, it also wasn’t disclosed that one of the quoted sources, Josepha Haden Chomphosy, is an employee of Matt Mulleweg’s company Automattic, instead incompletely describing her as “WordPress Executive Director”. She was quoted saying that there should be a focus on coopetition mindset in terms of data access: [Read more]