Security Review Catches Exploitable Arbitrary File Viewing Vulnerability in Eventin WordPress Plugin
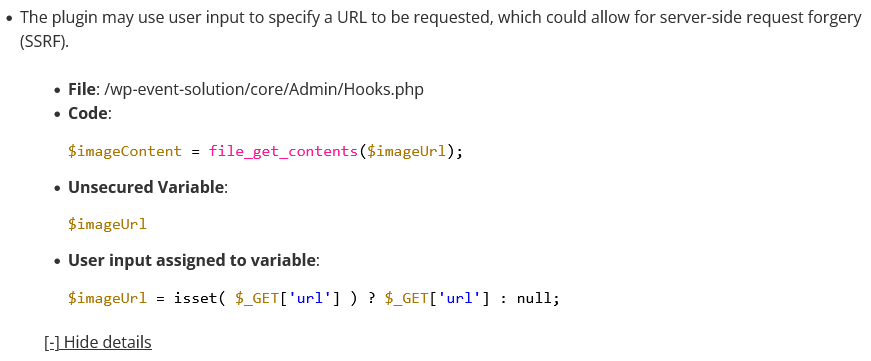
As part of starting a security review of the WordPress plugin Eventin after it was chosen by our customers to receive a review, we ran the plugin through our Plugin Security Checker. That identified the possibility of a server-side request forgery (SSRF) issue in the plugin: