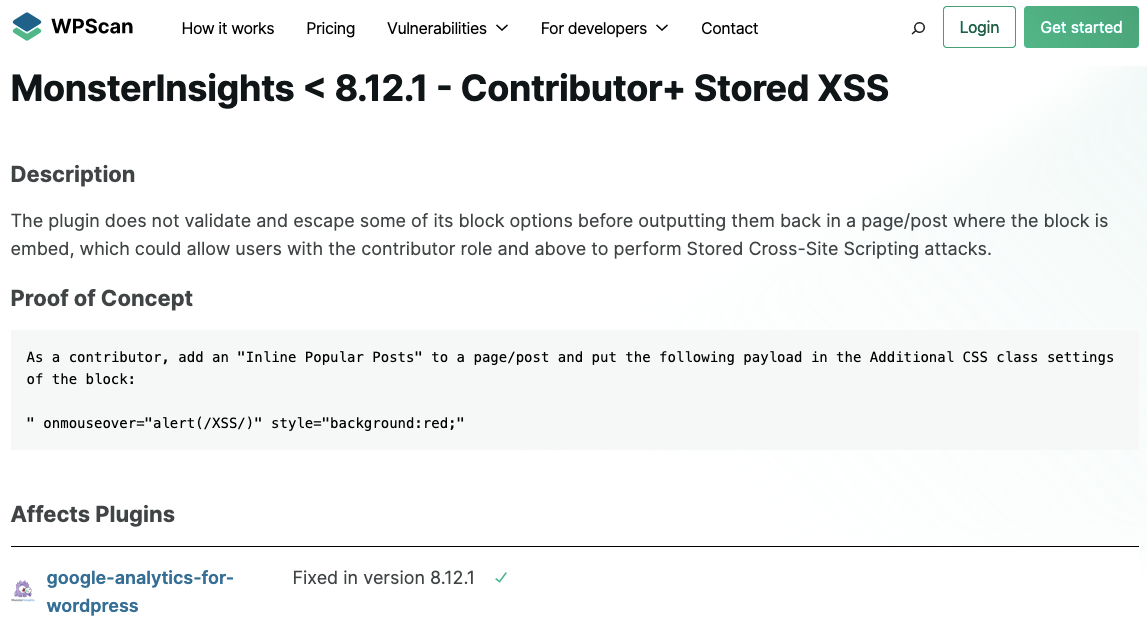
Wordfence’s Solution to Their Firewall Incorrectly Blocking Legitimate Request is to Disable Needed Protection
In our testing, the most popular security-only WordPress security plugin Wordfence Security fails to provide as much protection as other much less popular security plugins. Making the situation worse is that it introduces a significant performance penalty over security plugins that provide better protection. There is another problem with the plugin we have been running across instances of for years. Its firewall incorrectly blocks legitimate requests in situations where there doesn’t appear to be any reason it should have blocked the request.
Recently someone posted on the plugin’s support forum complaining that the firewall was blocking contact form submissions from the 5+ million install plugin Contact Form 7. They stated that what was causing it was the input containing the word “Data”. That seems odd. A Wordfence employee asked for a screenshot of the log information for the block and the poster replied with a screenshot that showed a request being blocked. [Read more]