WordPress Makes It Even Harder To Be Protected Against Vulnerabilities in WordPress Plugins
In dealing with issues surrounding vulnerabilities in WordPress plugins for too many years what we have come to find is that the people on the WordPress side of things seem to be less interested in actually protecting against them and more interested in covering up the problems, leaving to websites unnecessarily being hacked.
This appears, whether intentional or not, to start at the top. Here was Matt Mullenweg wrote in February of last year on what are the “biggest issues” when it comes to WordPress security:
What are the biggest issues to WordPress security?
A good order of priority based on impact would be:
-
Sites not updating core.
-
Sites not updating plugins.
-
Sites not updating themes.
-
Weak passwords, without brute-force protection or two-factor authentication.
-
Hosts (professional or ad-hoc) not scanning and fixing sites.
-
Hypothetical issues not seen in practice, which distract from the above existing priorities.
Strangely despite it being an ongoing and serious issue, this list treats unfixed vulnerabilities in WordPress plugins as being a “hypothetical” issue. The reality is very different. Not only are there currently plugins with 2.8+ million active installations that are publicly known to contain vulnerabilities that are still in the Plugin Directory (due to us being the only ones that apparently care about that), but there have been unfixed vulnerabilities in plugins that have been widely exploited, so simply keeping plugins up to date won’t protect websites. Far too many of those plugins never have been fixed, so there are still websites that are vulnerable years after the exploitation started.
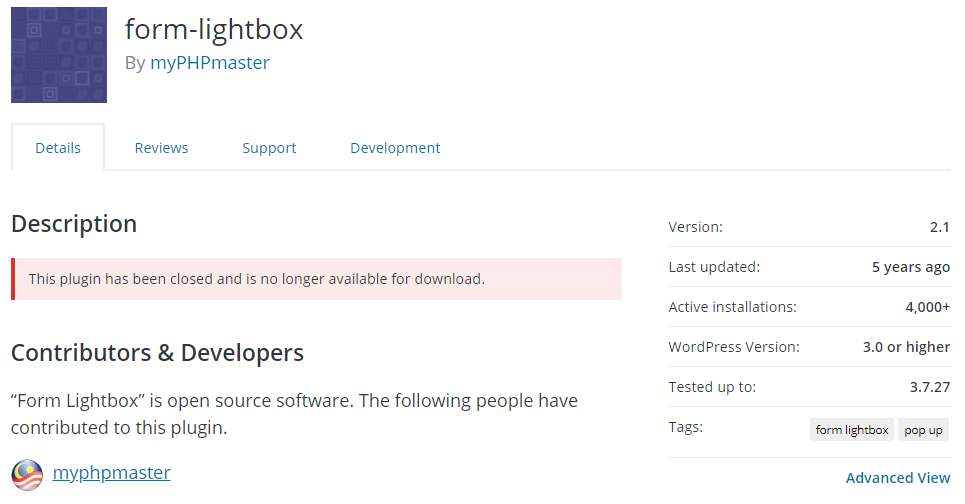
It isn’t like that is an issue that has never been brought up with anyone that has the power to change things. We actually tried to bring that up with someone that not only works directly for Matt Mullenweg, but is also one of six members of the team that handle the Plugin Directory, and who is in charge of the moderation of the WordPress Support Forum. Instead of having a discussion that could have lead to better handling of this type of situation our reply was deleted. The vulnerable plugin, Form Lightbox, that was being exploited that started the topic where our reply was deleted has itself never been fixed, despite wide exploitation of it over two years ago. Right now according to wordpress.org there are still 4,000 websites still using it:
That in itself should be scandalous, but it seems that no one on the WordPress side of things cares about that (if they did this could have been dealt with long ago).
Since the exploitation started there have been a couple of topics in the Support Forum from people still using the plugin and having issues with it, there is also a topic where someone points out how to get a hold of it since it has been removed.
The lack of willingness to deal with the problems isn’t a one off issue. For example, a moderator who has spearheaded the position of the Plugin Directory that WordPress shouldn’t warn when vulnerable plugins, which have been removed from the Plugin Directory, are being used, shut down a conversation about notifying people if they are using plugins removed from the Plugin Directory, for being “non-productive”.
In protest of the continued inappropriate behavior by the Support Forum moderators, which doesn’t just relate to not being able to discuss the poor handling of security of WordPress plugins, and their inability to have professional adult conversations to try to help them better work with the rest of the community, we have started full disclosing vulnerabilities in WordPress plugins and will continue until things change.
Unfortunately, but not surprisingly, considering their past behavior so far the people on the WordPress side of things haven’t decided so far that clean up their act would be the best solution, instead doing things like deleting our messages notifying developer of these full disclosures and then not bothering to even notify the developers of the issue, causing at least one of these publicly disclosed vulnerabilities to remain in the plugin even longer it would have if they had simply stayed out of the way. In another case there is a plugin with 30,000+ active installs for which they deleted our message notifying the developer of the vulnerability we disclosed last week, but have left the known vulnerable plugin in the Plugin Directory so far.
They have now made the situation with these unfixed exploited vulnerabilities even worse. While they have been perfectly fine with websites being hacked, we have provided a plugin Plugin Vulnerabilities, which in addition to working with our service, includes in it free data on any vulnerabilities we are aware are being exploited, and they decided today to remove that from the Plugin Directory. If someone were to have installed that plugin, for example they would have been warned that they were using a vulnerable version of the Form Lightbox plugin mentioned earlier. They also removed our other plugin plugins, including one used on 20,000+ websites to make sure there plugins are kept up to date. That is exactly the kind of counterproductive behavior that actually lead to us taking the step of starting to full disclose these vulnerabilities, so it isn’t going to stop it. The moderators need to stop acting inappropriately and they should do it right now.
We would please ask the people on the WordPress side of thing to finally realize what you have been doing isn’t actually in the best interest of the community and actually work with those that have been trying to help you, instead of taking counterproductive actions that just make things worse. You don’t need to look any farther than those 4,000+ websites still using Form Lightbox to see that what you have been doing isn’t working and things need to change.
It wouldn’t be hard to change things if you guys decide to be part of the solution, but it does require that, as, for example, right now if you are doing the manual security reviews of WordPress plugin you claim to, they are missing easily exploited vulnerabilities. That is something we can easily help you avoid (and have offered to help with in the past), but it requires that you be willing to cooperate with others instead of what you are doing now, which in that case clearly isn’t leading to the best result.
Might be because you post like a troll. Perhaps if you were less of a jerk.
It doesn’t sound like you understand what trolling even is, but assuming that we even were in fact posting “like a troll”, what would that have to do with leaving 4,000+ websites with a plugin that contains an unfixed vulnerability, which is known to have been exploited, open to being hacked?