You Need to Make Sure Proof of Concepts for Vulnerabilities in WordPress Plugins You Use Have Been Tested
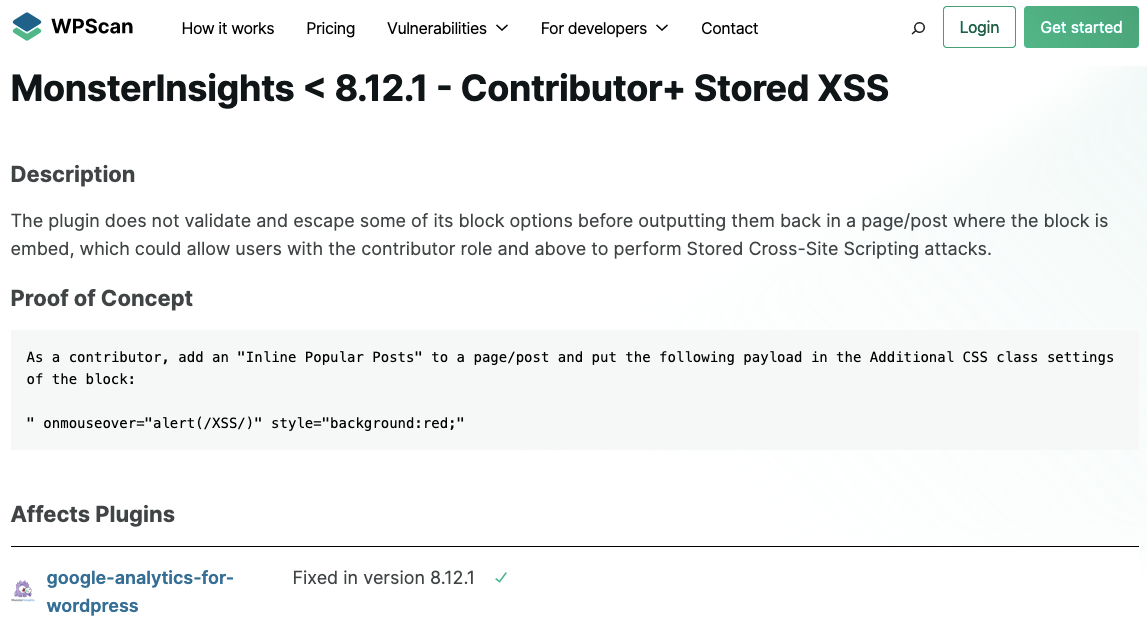
Are you relying on a security provider to warn about vulnerabilities in WordPress plugins you use? Are you not testing out the proof of concepts for those vulnerabilities because the security provider claims they are verifying things for you or because you don’t have the capability to do that? If you answered yes to both of those, we have bad news for you, as many of those providers are not doing that testing either, leaving websites vulnerable running still vulnerable plugins and hackers with a info on how to exploit them. A recent example of that involves a plugin with 20,000+ installs where most data providers recently claimed that there was a known vulnerability in the plugin that had been fixed, despite the proof of concept contradicting that.
Here was the original source of the claim, Automattic’s WPScan, making it (and claiming they had verified their information): [Read more]